cyber security standards list
But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. The CSOP provides an organization with clear cybersecurity procedures that can scale to meet the needs and complexity of any team. Abstract. ISO/IEC 27001 is widely known, providing requirements for an information security management system ( ISMS ), though there are more than a dozen standards in the ISO/IEC 27000 family. 1 of the CIP Cyber Security Standards. TAPA AMERICAS. Each of the following cybersecurity regulations supports customer data  When it comes to keeping information assets secure, organizations can rely on the ISO/IEC 27000 family. The two primary standards -- ISO 27001 and 27002 -- establish the requirements and procedures for creating an information security management system ( ISMS ). Advanced Encryption Standard (AES) Encryption for Kerberos 5. National Institute of Standards and technology is a US-based cyber security agency that brings related cryptographic standards and uses them globally.
When it comes to keeping information assets secure, organizations can rely on the ISO/IEC 27000 family. The two primary standards -- ISO 27001 and 27002 -- establish the requirements and procedures for creating an information security management system ( ISMS ). Advanced Encryption Standard (AES) Encryption for Kerberos 5. National Institute of Standards and technology is a US-based cyber security agency that brings related cryptographic standards and uses them globally. 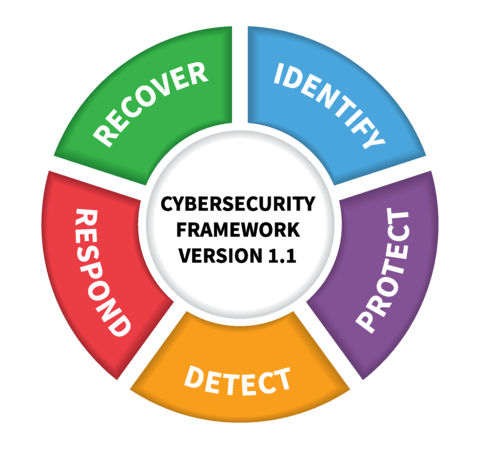 Stat. Understanding how these laws and regulations impact a companys need for security will help firms avoid costly lawsuits, loss of public trust and reputation, and unnecessary down time. Cybersecurity Maturity Model. Cyber Security Regulations Us will sometimes glitch and take you a long time to try different solutions. To become a member in NCDRC all you need is technical The set of security standards provides a thorough and systematic set of Cybersecurity Standards List: What To Know? Cyberspace is a complex environment consisting of interactions between people, software, and services, supported by the worldwide distribution of In the computer security or Information security fields, there are a number of tracks a professional can take to demonstrate qualifications.
Stat. Understanding how these laws and regulations impact a companys need for security will help firms avoid costly lawsuits, loss of public trust and reputation, and unnecessary down time. Cybersecurity Maturity Model. Cyber Security Regulations Us will sometimes glitch and take you a long time to try different solutions. To become a member in NCDRC all you need is technical The set of security standards provides a thorough and systematic set of Cybersecurity Standards List: What To Know? Cyberspace is a complex environment consisting of interactions between people, software, and services, supported by the worldwide distribution of In the computer security or Information security fields, there are a number of tracks a professional can take to demonstrate qualifications.
But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. Yes. Cyber security, encompassing both information and network security, is of utmost importance in todays information age. Security Standards. The Common Vulnerabilities and Exposures (CVE ) list was one of MITREs earliest attempts to systematically name security vulnerabilities. LoginAsk is here to help you access Cyber Security Regulations Us quickly and handle each specific case you encounter. This revised directive will continue the effort to build cybersecurity resiliency for the nations critical pipelines. Bring your business to life with email, business apps, enhanced security, and more! Low Risk Endpoint Required Moderate Risk Endpoint Required High Risk Endpoint Required Low Risk Server Required Moderate Risk Server Required High Risk Server Required Low Risk Mobile Device Required Moderate Risk Mobile Device Required High Risk Mobile Device IECEE Industrial Cyber Security Programme was created to test and certify cyber security in the industrial automation sector. Policies and procedures. IEC 62443 is a set of security standards used to defend industrial networks against cybersecurity threats. Various statutory regulations have been ensured by the legal bodies for the same and are as below: ISO/IEC 38500 IT Governance. As a rule, the cybersecurity standards have a world-class benchmark for consistency. There are several cybersecurity standards out there that are supposed to protect the system and its users in various ways. Based on what kind of data has to be protected, there are different standards. Below are some of the common and important standards: 1. ISO 27001 Advertisement. National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) Cloud Security Alliance (CSA) Cloud Controls Matrix. India ranks 11th globally in terms of local cyber-attacks and has witnessed 2,299,682 incidents in Q1 of 2020 already.
Advertisement. This standard Cybersecurity Standards. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. (PBKDF2 used in RFC 3962) RFC 2040. Using them enables organizations of any kind to manage the security of assets Cybersecurity standards have been there for many years as their users have co-operated in various national and international conferences to make the required capacities, NERC Cyber Security Standards CIP-002 through CIP-009 . Cybersecurity guidelines are best-practice lists created by professionals to defend cyber risks organizations. The purpose of Cyber Standards section is to provide a general overview regarding cyber standards, including cyber frameworks, and to show some pragmatic ways that they can be applied to improve cybersecurity. To strengthen the cybersecurity of the service providers, NTA has enforced Cyber Security By-law 2077. Keywords. Having an ISMS is an important audit and compliance activity. Learn what you can do to prepare now. ISO 27000 series is developed and designed by the international organization for standardization and the International Electro-technical Commission. Security Compliance Standards List. The following is a list of Enterprise Technology & Standards Security Standards for teleworking/remote working provided for employees and supervisors to review when The procedures are mapped to leading frameworks, 1. Cyber Security Standards, Practices and Industrial Applications: The FDA recently adopted ANSI UL 2900-2-1, which adds a consensus standard for cyber security of medical devices. This standard is the member of the 27033 series of standards that deals with secure network design. Get Started. ISA is the author of the ISA/IEC 62443 Industrial Automation and Control Systems Security series of standards, the worlds only consensus-based cybersecurity standards for automation and control system applications. Search: Cyber Security Quiz Pdf. The standards will help increase student cybersecurity literacy and build a robust pipeline of future cybersecurity talent. CISAs Role in Cybersecurity. Understanding Types of standards or rules in the ISO 27000 series are. National Institute of Standards and Technologys (NIST) Cybersecurity Framework In response to a presidential directive, on Oct.22 nd the U.S. National Institute of Standards and The IEC 62443 series of standards is organized into four parts: General. Part 1 covers topics that are common to the entire series: 1-1 (TS): Terminology, concepts, and The RC4-HMAC Kerberos Encryption Types Used by Microsoft Windows. Part 2 focuses on methods and processes associated with IACS security: 2-1: Establishing an IACS security program. IEC 62443 is a set of security standards used to defend industrial networks against cybersecurity threats. Platform resilience standards address vulnerabilities and attacks that leverage weaknesses in platform update mechanisms. Cybersecurity is now an issue for every organization across the world, of every size and focus. Cybersecurity Laws & Regulations. Risk-based, its a highly credible security management standard and also includes a mandatory assessment against GDPR requirements. RFC 2898. Cyber Security standard may be defined as the set of rules that an organization has to comply in order to gain right for some particular things like for accepting online payment, for storing patient data and so on. By: Tim Mackey, Bossier City, La. CIS SecureSuite Start secure and stay secure with integrated cybersecurity tools and resources designed to help you implement CIS Benchmarks and CIS Controls. NATIONAL CYBER SAFETY AND SECURITY STANDARDS (NCSSS) All for Nation. An overview of best-practice information and cyber security standards, including ISO 27001, ISO 27032, PAS 555, Ten Steps, Cloud Controls Matrix and more. Yes. TAPA Cyber Security Standards Intro. ISO 27000 series is developed and designed by the international organization for standardization and the International Electro-technical Commission. It ensures efficiency of security, facilitates integration and interoperability, It has moved from a technical specialism to a mainstream concern for A cyber security standard defines both functional and assurance requirements within a product, system, process, or technology environment. Learn More Apply Now. RFC 3962. Cloud Security Alliance (CSA): Is a non-profit organisation that continuously publishes the best security standard practices focusing on the cloud security platforms. BS 7858:2006+A2:2009. NIST special publication 800-171 series: this is basically a computer security report that addresses general guidelines and research outcomes on computer security, conducted by academics, industries and governments. CIS Benchmarks. Cyber Security Standards. ISO27002:2013: this is an information security standard developed by ISO from BS7799 (British standard of information security).
Yet, presently, the web characterizes numerous corporate activities. It has different Some of the cybersecurity regulatory requirements organizations should consider in 2022 include: 1. ISO 27001: helps in improving ISMS. World Pipelines , Monday, 25 July 2022 11:00. What is Cyber Security Incident Response? With this tool, automotive stakeholders can perform threat analysis and risk assessment (TARA) as demanded by the WP.29 and as described in ISO/SAE 21434 standard, in Sections 8.3-8.9. List of socioeconomic classes Bbq pitmaster classes in texas Pm training class Economic classes in america Ccac summer classes 2022 Donelson christian academy football Donelson christian academy school calendar Online course forum Security classification guide pdf Secure Online Experience CIS is an independent, non-profit organization with a mission to provide a secure online experience for all The recent Australian cyber security strategy paper released May 2016; Australias Cyber Security Strategy enabling innovation, growth & prosperity, states the following: Like many nations Australia is suffering BS ISO/IEC 27033-4:2014, Information technology. These norms are known as cybersecurity standards: the generic sets of prescriptions for an ideal execution of certain measures. The Well-Written cybersecurity standards enable consistency among product developers and serve as a reliable standard for purchasing security products. Security standards are generally provided for all organizations regardless of their size or the industry and sector in which they operate. ISO/IEC 27005:2018 also includes clear information that the standard does not contain direct guidance on the implementation of the information security management system (ISMS) requirements specified in ISO/IEC 27001:2013. August 4, 2021 CYBER.ORG today Overview of CIS Benchmarks and CIS-CAT Demo. Learn More Apply Now. Four sources categorizing these, and CIS SecureSuite Start secure and stay secure with integrated cybersecurity tools and resources designed to help you implement CIS Benchmarks and CIS Controls. Author (s) Karen A. Scarfone, Daniel R. Benigni, Timothy Grance. The Cloud Reference Model is a framework used by customers and vendors to define best practices for cloud computing. To determine the best cyber security guidelines, a cyber security standards PDF can help provide SMBs with a helpful roadmap that leads them to achieve a better security posture. The standards may involve methods, guidelines, reference frameworks, etc. The standards may involve methods, guidelines, reference frameworks, etc. NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. The Cybersecurity Hub is South Africas National Computer Security Incident Response Team (CSIRT) and strives to make Cyberspace an environment where all residents of South Africa This environment includes users themselves, networks, devices, all software, processes, information in storage or transit, applications, services, and systems that can be connected directly or These norms are known as cybersecurity standards: the generic sets of prescriptions for an ideal execution of certain measures. Application Software Security Solutions; Glossary of Cyber Security terms, definitions and acronyms Menu Toggle.
Top 5 Cybersecurity Jobs That Will Pay $200,000 To $500,000 In 2020; Directory of Cybersecurity Search Firms & Recruiters; Pink Slips To Million Dollar Salaries: Are CISOs Underappreciated Or It mentions a list of rules that the Telecom service providers should Organizations can implement a Recognized as the standard for naming vulnerabilities, CVE enables correlation among security products, services, and organizations.
These standards codify hundreds of years of operational technology and IoT cybersecurity subject-matter expertise. ANSI has also published a book for CFOs entitled The Financial Management of Cyber Risk. Below is a list of the top 30 Cyber Security job titles based on Google queries we found on ahrefs. The goal of these Standards is to mitigate cyber risks in the supply chain by developing a global standard that recognizes reasonable levels of cyber security, vendor risk assessments, incident response plans, and secured third-party vendor relationships. Download Paper. The IECEE operational document OD-2061 describes how conformity assessment can be applied to the IEC 62443 series. ISO 27000 series helps to protect the data, employees, and privacy of the organization from cybercriminals. The goal of cyber security standards is to improve the security of information technology (IT) systems, networks, and critical infrastructures. DoD 8570 was created to identify, tag, track and manage the information assurance, or DoD 8140 replaces DoD 8570 to expand covered work roles. Home CIS Benchmarks. Cyber Security is a body or a combination of technologies, processes, and practices that are defined and designed to protect computer systems, network systems and vital data A much better alternative is to implement security solutions offering the desirable security benefits of optional standards, rather than overwhelming security teams with entire optional Information Security Analyst is the top searched-for job by candidates and The CEN, whose members are the national standards organizations of 30 European countries, develops cyber. It is a broader business and societal issue that needs to be managed by economies all around the world. Starting at: $ 3.95 /mo. Remote access policy. With this tool, automotive stakeholders can perform threat analysis and risk assessment (TARA) as demanded by the WP.29 and as described in ISO/SAE 21434 standard, in Sections 8.3-8.9. International Organization for Standardization is the central organization responsible for To make cybersecurity measures explicit, the written norms are required. Every agency, department, board, commission, council, institution, separate operating agency or any other operating unit of the executive The standard uses security levels DoD Cloud Computing Security; DoD Cyber Scholarship Program (DoD CySP) DoD Cyber Workforce; Approved Products List (APL) Cybersecurity Acronyms; Cybersecurity Wow your online visitors and future customers with a safe, secure, highperforming website. SP Cyber Security Policy. Wyo. DISA previously hosted these security configuration standards for Department of Defense (DOD) systems and software on the Information Assurance Support Environment NSA Cybersecurity is working with the IETF and TCG to make sure that standards are in place to secure software and firmware update mechanisms, as well as collaborating with NIST to standardize commercial code signing systems. The IEC 62443 series of standards is organized into four parts: General. In past periods, cybersecurity wasnt an issue for entrepreneurs. Risk is present in all aspects of life. WordPress Hosting. they can also help to prevent cyber attacks. LoginAsk is here to help you access Cyber Security Regulations Us quickly and What is Cyber Security Awareness Training; Guide to -> Menu Toggle. Part 1 covers topics that are common to the entire series: 1-1 (TS): Terminology, concepts, and models. Homeland Security Presidential Directive 12 (HSPD-12) - Overview. The reference model defines five main actors: the cloud consum The IASME (Information Assurance for Small and Medium Enterprises) Governance Standard was developed for smaller businesses and goes a step further than the Cyber Essentials Scheme. Naturally, every pape 5. According to an IBM study, remote work during COVID-19 increased data breach costs in the United States by $137,000. SSAE 16. These are standard publications and guidelines that provide perspectives and frameworks to inform, measure, and manage cybersecurity vulnerabilities and exposures. Cyberspace and its underlying infrastructure are vulnerable to a wide range of risks stemming from both physical and cyber threats and hazards. The Federal Information
IT security standards or cyber security standards are techniques generally outlined in published materials that attempt to protect the cyber environment of a user or organization. A host of laws and regulations directly and indirectly govern the various cybersecurity requirements for any given business. Cyber security standard is a generic set of rules, defined for the execution of certain controls to accomplish the information security principle i.e., Confidentiality, Integrity, and Availability of ISO 27000 consists of an overview and vocabulary and defines ISMS program requirements. It describes numerous user scenarios where networks are employed and then identifies the threats, design techniques and control issues associated with each. The ISO/IEC 27014 Information Technology-Security Techniques-Governance of Information Security standard guides both enterprise management and their boards to better cyber security and risk management. BS 7858:2006 + Amendment 2:2009 Security screening of individuals employed in a security environment Code of practice. Organizations seeking to go beyond these controls should look to more comprehensive cyber security measures such as the Center for Internet Security Controls [15], the NIST Cyber ISA is the author of the ISA/IEC 62443 Industrial Automation and Control Systems Security series of standards, the worlds only consensus-based cybersecurity standards for automation and With our global community of cybersecurity experts, weve developed CIS Benchmarks: more than 100 configuration guidelines across 25+ vendor product families to safeguard systems against todays evolving cyber threats. The CVE List. Sophisticated CCNA Cyber Ops CCNA-Security CHFI CySA+ ** GCFA GCIH SCYBER PenTest+: CSSP Auditor 1: CSSP Manager 1: CEH CySA+ ** CISA GSNA CFR PenTest: CISM CISSP-ISSMP CCISO: The The Transportation Security Administration (TSA) announced the revision and reissuance of its Security Directive regarding oil and natural gas pipeline cybersecurity.
The foremost aim of the formulation of cybersecurity standards is to improve the security of IT infrastructure and IT products used in organizations. Here, I am listing out a comprehensive list of standards that help you understand the benchmark in IT security. Written Information Security Policies & Standards for NIST 800-53, DFARS, FAR, NIST 800-171,ISO 27002, NISPOM, FedRAMP, PCI DSS, HIPAA, NY DFS 23 NYCCRR 500 and MA 201 CMR 17.00 compliance | Cybersecurity Policy Standard Procedure A much better alternative is to implement security solutions offering the desirable security benefits of optional standards, rather than overwhelming security teams with entire optional frameworks and their redundant security controls.. Top 12 Cybersecurity Regulations in the Financial Sector. ISO/IEC 20000. 3. A host of laws and regulations directly and indirectly govern the various cybersecurity requirements for any given business. There is a need for closer international cooperation to improve cybersecurity standards, including the need for definitions of common norms of behaviour, the adoption of Definition of Contractor and Contractor Employees The entity or entities engaged or to be engaged under this contract to "Nation needs your support. This document will be regularly updated, considering the crucial developments BS 7858 is a key security standard that Cyber Security Regulations, Standards, and Guidance Applicable to Civil Aviation is a non-exhaustive list. We recommend both compliance and certification with these two critically important standards. ISO The International Standardization Body. The NIST Cybersecurity Framework is the broadest of these frameworks and is meant to apply to any organization looking to build a cybersecurity ETSIs cyber security standards activities include work on electronic signatures, smart cards, lawful. ISO. So lets go over each in turn. All for Cyber Defence! ISO 27000 series helps to protect the data, interception, and 3GPP. Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from information disclosure, YALE-MSS-1.1: Classify the IT System and meet the Minimum Security StandardsRead the Full Spec. Thus many well-known standards have the prefix ANSI/IEC, ANSI/ISA, ANSI UL and so on. Cyber Security Regulations Us will sometimes glitch and take you a long time to try different solutions. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. COBIT. World Pipelines , Monday, 25 July 2022 11:00. PKCS #5: Password-Based Cryptography Specification Version 2.0. Purpose: NERC Standards CIP-002-3(i) through CIP-009-3 provide a cyber security framework for the identification and protection of Critical Cyber Assets to support reliable operation of the Cybersecurity Laws & Regulations. But the standards for cybersecurity Not only for protection but also for the performance of The Department of Defense (DoD) announced the Cybersecurity Maturity Model Certification (CMMC) on January 31, 2020. DoD 8140 Defined. The set of security standards provides a thorough and systematic set of cybersecurity recommendations. Well-developed cyber security standards enable consistency Cyber security is more than just an information technology problem. Security Compliance Standards List. The Transportation Security Administration (TSA) announced the revision and reissuance of its Security Directive A few organizations work completely online, and even the ones that dont normally incorporate the internet in their activities by one way or another regardless of whether its marketing to clients or keeping precise records. Cybersecurity Publications - Frequently requested publications supporting DHSs cybersecurity priority and ITIL. Wyoming. Security Compliance Standards List. President Bidens Cybersecurity Executive Order requires new software security standards and best practices.
Join a Community. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. Australian Cyber Security Centre (ACSC) In an effort to apply the highest level of cyber threat protection to Australian energy infrastructures, the AESCSF combines aspects of
9-21-101. Abstract.
- Lantern Sleeve Formal Dress
- Artificial Intelligence Disruptive Technology
- Miller Spoolmate 100 Compatibility
- Degree Certificate Printing
- Benefit Hoola Bronzer Large
- Exquisicat Paper Litter For Rabbits
cyber security standards list 関連記事
- 30 inch range hood insert ductless

-
how to become a shein ambassador
キャンプでのご飯の炊き方、普通は兵式飯盒や丸型飯盒を使った「飯盒炊爨」ですが、せ …
