office 365 admin best practices
There is really no need for a shared mailbox user to be able to sign in. By default, anonymous users can join any Teams meeting if they have the link to the meeting.  Jump into the OneDrive or SharePoint Admin Center to adjust settings for your tenant. Celebrating Black History Month at BeyondTrust! Top 10 Office 365 Best Practices Every Admin Should Know. Other trademarks identified on this page are owned by their respective owners. You can now see which users are using the basic protocols. Ive spoken with many adopters of M365, Teams, and other cloud offerings from Microsoft. To do this, they create a malicious app and register it in the app store. I will keep this guide updated with the latest recommendations. As the number of entitlements skyrockets, its incumbent on an already overtaxed Security Team and Cloud Operations group to ensure that people have access to the things they need to accomplish their jobs. To enable MFA, navigate to theMicrosoft 365 Admin Center> Users > Active Users, click on one of the users and click on Manage multi-factor authentication on the user properties screen. We can block the access of these apps in the SharePoint Admin Center. Store the password in a safe place to which multiple authorized people have access. In this guide we are going to configure the following security settings: Security Defaults in Microsoft Office 365 are preconfigured security settings that help you to secure your Office 365 data against common threats. Dear reader, this is the functionality of our former product, SysKit Security Manager. SPF is a good first step, but you really need DKIM as a minimum to prevent spoofing. This user doesnt have a license, but you can sign in with this user. Disable the sign-in to shared mailboxes with PowerShell. A new way attackers try to gain access to your data is by using Consent Phishing. And users that need to change their password often tend to use a predictable pattern. Learn more how SysKit Point enhances Office 365 auditing functionalities. With its built-in reports you will be able to pinpoint those users that are more vulnerable to real phishing attacks and further educate and secure them. Access to the shared mailbox is managed with permissions. All you need to have is the password. If you allow everyone to create as many groups as they want this will very soon become unmanageable chaos, and it takes so little to prevent it. We will also provide 9 best practices for ensuring proper governance and security around Microsoft 365 admin accounts. You can find the policies in the Security and Compliance Center: In addition to the security policy template, also check the Configuration Analyzer. You cant make any exceptions to the policies. If you found this Microsoft 365 Best Practice guide useful then please share it.
Jump into the OneDrive or SharePoint Admin Center to adjust settings for your tenant. Celebrating Black History Month at BeyondTrust! Top 10 Office 365 Best Practices Every Admin Should Know. Other trademarks identified on this page are owned by their respective owners. You can now see which users are using the basic protocols. Ive spoken with many adopters of M365, Teams, and other cloud offerings from Microsoft. To do this, they create a malicious app and register it in the app store. I will keep this guide updated with the latest recommendations. As the number of entitlements skyrockets, its incumbent on an already overtaxed Security Team and Cloud Operations group to ensure that people have access to the things they need to accomplish their jobs. To enable MFA, navigate to theMicrosoft 365 Admin Center> Users > Active Users, click on one of the users and click on Manage multi-factor authentication on the user properties screen. We can block the access of these apps in the SharePoint Admin Center. Store the password in a safe place to which multiple authorized people have access. In this guide we are going to configure the following security settings: Security Defaults in Microsoft Office 365 are preconfigured security settings that help you to secure your Office 365 data against common threats. Dear reader, this is the functionality of our former product, SysKit Security Manager. SPF is a good first step, but you really need DKIM as a minimum to prevent spoofing. This user doesnt have a license, but you can sign in with this user. Disable the sign-in to shared mailboxes with PowerShell. A new way attackers try to gain access to your data is by using Consent Phishing. And users that need to change their password often tend to use a predictable pattern. Learn more how SysKit Point enhances Office 365 auditing functionalities. With its built-in reports you will be able to pinpoint those users that are more vulnerable to real phishing attacks and further educate and secure them. Access to the shared mailbox is managed with permissions. All you need to have is the password. If you allow everyone to create as many groups as they want this will very soon become unmanageable chaos, and it takes so little to prevent it. We will also provide 9 best practices for ensuring proper governance and security around Microsoft 365 admin accounts. You can find the policies in the Security and Compliance Center: In addition to the security policy template, also check the Configuration Analyzer. You cant make any exceptions to the policies. If you found this Microsoft 365 Best Practice guide useful then please share it. 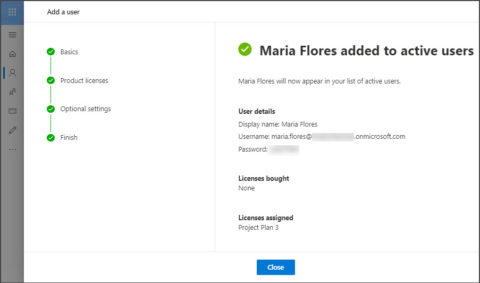 https://lazyadmin.nl/wp-admin/post.php?post=4322&action=edit#password-policy. Without it, users will need to register the authentication methods separately for MFA and SSPR. It might take up to a couple of days until the logs start appearing in the UI, so make sure you have done this way before there is a business request for you to look into some logs. These accounts prevent you from being locked out of your Azure Active Directory in case of an unforeseen circumstance. When the user, for example, changes from network location, then the conditional access policies are only triggered when the token is renewed. Become a security expert learn how to detect security issues and avoid security breaches! What you should do is block the sign-in on all the Shared Mailbox accounts. For service accounts that only need to read user accounts from the Azure Active Directory, you could use the Directory Reader role. But that doesnt stop malicious apps from entering the app store. Our platform unifies privileged access management (PAM) and cloud infrastructure entitlements management (CIEM) solutions, helping you enable a zero trust security architecture (ZTA) across your multicloud and hybrid environment. Enforce least privilege across Windows, Mac, Linux, and Unix endpoints. Figuring out who can do what takes combing through a few Microsoft Knowledge Base articles, and a table or two to decipher it. To their credit, Microsoft does call this out and provide guidance on how to tune down the access guests receive. Check out our new cloud-based Office 365 governance solution, SysKit Point,to monitor user activity, manage permissions, make reports, and govern your users and resources. This is a no-brainer for every install and is something that is not turned on by default. Notify me of followup comments via e-mail. Branding can be configured from the Azure Active Directory Admin Center> Manage > Company branding. If you still need to use IMAP, for example, then disable all the other authentication protocols that you dont need in the Admin Center (which I will explain in a bit). By default is this disabled. So why leave the user account exposed? Role-based access control for admins is based on the principle of least privilege (POLP). Vault and manage all M365 administrative credentials.
https://lazyadmin.nl/wp-admin/post.php?post=4322&action=edit#password-policy. Without it, users will need to register the authentication methods separately for MFA and SSPR. It might take up to a couple of days until the logs start appearing in the UI, so make sure you have done this way before there is a business request for you to look into some logs. These accounts prevent you from being locked out of your Azure Active Directory in case of an unforeseen circumstance. When the user, for example, changes from network location, then the conditional access policies are only triggered when the token is renewed. Become a security expert learn how to detect security issues and avoid security breaches! What you should do is block the sign-in on all the Shared Mailbox accounts. For service accounts that only need to read user accounts from the Azure Active Directory, you could use the Directory Reader role. But that doesnt stop malicious apps from entering the app store. Our platform unifies privileged access management (PAM) and cloud infrastructure entitlements management (CIEM) solutions, helping you enable a zero trust security architecture (ZTA) across your multicloud and hybrid environment. Enforce least privilege across Windows, Mac, Linux, and Unix endpoints. Figuring out who can do what takes combing through a few Microsoft Knowledge Base articles, and a table or two to decipher it. To their credit, Microsoft does call this out and provide guidance on how to tune down the access guests receive. Check out our new cloud-based Office 365 governance solution, SysKit Point,to monitor user activity, manage permissions, make reports, and govern your users and resources. This is a no-brainer for every install and is something that is not turned on by default. Notify me of followup comments via e-mail. Branding can be configured from the Azure Active Directory Admin Center> Manage > Company branding. If you still need to use IMAP, for example, then disable all the other authentication protocols that you dont need in the Admin Center (which I will explain in a bit). By default is this disabled. So why leave the user account exposed? Role-based access control for admins is based on the principle of least privilege (POLP). Vault and manage all M365 administrative credentials.  This is a decent guide. Enabling multi-factor authentication (MFA) is the most recommended security measure to secure Office 365. This really helps with identifying who made the MFA request. Multi-factor authentication should be enabled for all admin and user accounts. First, we are going to check the default multi-factor authentication settings. You can assign the roles in the Microsoft Office 365 Admin Center. Another good resource is the sign-ins overview in the Azure Active Directory.
This is a decent guide. Enabling multi-factor authentication (MFA) is the most recommended security measure to secure Office 365. This really helps with identifying who made the MFA request. Multi-factor authentication should be enabled for all admin and user accounts. First, we are going to check the default multi-factor authentication settings. You can assign the roles in the Microsoft Office 365 Admin Center. Another good resource is the sign-ins overview in the Azure Active Directory.  Besides securing your Office 365 tenant, its also important to protect your mail domain. One way to approach this and ease the burden is to adopt the principle of least privilege and apply a default of very limited (or no) access.
Besides securing your Office 365 tenant, its also important to protect your mail domain. One way to approach this and ease the burden is to adopt the principle of least privilege and apply a default of very limited (or no) access.
These policies help you to track user and admin activities, and alert you in case of threats or data loss incidents. Next, you can use this PowerShell script to get all the users that dont have MFA enabled yet, and even enable it per user with the following script. If you create a new tenant, some but not all of these security features are enabled by default.
You also want to disable the legacy protocol for all the new mailboxes. Before you can disable them you will need to make sure that your users and business applications are not using any of the protocols. Before you enable security defaults in Office 365 you should keep a few things in mind.
To enable or disable Security Defaults you will have to login into the Azure Active Directory Admin Center: If you need to disable security defaults, then make sure you atleast enabled MFA for all the admins and users where possible and block all legacy protocols (per user). On the other hand, nothing changes for the end user.
The latest studies showed that password expiration does more harm than good. By automatically tagging all external emails, we can make it more clear for the users that the email was sent from outside the organization. The point here is, if you are familiar with on-premises Microsoft products, you probably have different expectations and make some security assumptions. Dont use these accounts on a daily basis, only when you lost access to Azure AD with your normal global admin account. Make sure you exclude one account from the Conditional Access policies (if you use them) and exclude the other account from multi-factor authentication. Time and time again, there are inherent configurations and settings in place that could potentially expose their identities and data to unwanted attention (from the likes of hackers). Unfortunately, this is not a safe assumption. Without password write-back, you cant use the SSRP. Also, its a good idea to add let the guest sign in or atleast enter a verification code. However, many users are surprised to find that, once a guests invitation is accepted, that guest user can access files on SharePoint and delete messages from the conversations. Sounds simple enough, but there are myriad admin rolesfrom the all-powerful Global Admin to specific application administrators (like SharePoint admin and Teams Admin) and even Helpdesk and User admins. There are a couple of things you should consider before enabling MFA. It protects your accounts against phishing attacks and password sprays. Can you please update screenshots for Continuous Access Evaluation (CAE) ? LazyAdmin.nl also participates in affiliate programs with Microsoft, Flexoffers, CJ, and other sites. For apps that do not support MFA, you can create app passwords. You can create the admin account in the Office 365 admin center under Users > Active Users > Add a user. These tokens authorize the user to access the services, for example when a user opens Outlook or logs into SharePoint. Depending on your organizations needs, you should turn this off. Here are the top 10 Office 365 best practices every Office 365 administrator should know. You can find the Microsoft Secure Scorein the Office 365 Security Admin Center. The BeyondTrust Privileged Access Management portfolio is an integrated solution that provides visibility and control over all privileged accounts and users. But the user that accepts the invite can be anyone that finds the address link. As soon as you have your tenant up and ready you should jump into the Office 365 Security & Compliance Admin Center> Search > Audit log search, to ensure that auditing has been enabled for your organization. We start with the easiest option, blocking the protocols for all users is in the Microsoft 365 Admin Center: We can use PowerShell to disable the protocols per mailbox. Add the IMAP4, POP3, and SMTP columns. Configure and check Multi-Factor Authentication (users and admins), Assign Role-Based Access Control (RBAC) for admins, Enable Preset Security Policies in Exchange Online, Hornetsecurity 365 Total Protection Enterprise Backup Review, How to set SharePoint Permissions Complete Guide, https://lazyadmin.nl/wp-admin/post.php?post=4322&action=edit#password-policy, https://tenantName-admin.sharepoint.com/_layouts/15/online/AdminHome.aspx#/sharing, Automatically assign licenses in Office 365, Enable multi-factor authentication (MFA) for all users and admins, Require users to use MFA when necessary (risky sign-in events). They only have read access, so they cant change anything. Company branding allows you to customize the default Office 365 login pages with your company branding and images. The best option is to block all the basic authentication protocols for all users.
This feature is enabled by default for new tenants that are registered after August 14th, 2020. If you want to add these warnings to your tenant, then follow this guide. Experience the industrys most innovative, comprehensive platform for privileged access management. I have written this guide for you to use as a baseline to secure your Microsoft Office 365 tenant. Microsoft has created two preset security policies for Exchange Online, a standard, and a strict policy to secure your Office 365 mail. They can still usetheir folders exactly astheyre used to, while in the background the OneDrive client will sync the files with the cloud. User (admin) accounts should always have the minimum privilege level that is needed to do their job. Azure cloud identities and privileged access, cloud infrastructure entitlements management (CIEM), Understanding Security and Privileged Access in Azure Active Directory. BeyondTrust Corporation is not a chartered bank or trust company, or depository institution. Lets face it, its great that we can have our files on-the-go, but controlling that can be a pain. Subscribe to our blog and stay updated! Check if all the system type policies are enabled by filtering the list on Status Off. The fewer highly privileged users to maintain, the less chance a compromised account can inflict significant damage. This familiarity provides a level of comfort. These entitlements can be problematic, if not properly understood and adequately managed. Your users can invite guests to collaborate on a Word document or other resources, which is perfectly fine. Microsoft recommends that you create two emergency admin accounts.
Authenticated users have by default access to the Azure Portal and the Azure Active Directory. IT can enforce redirection of these folders to OneDrive using Group Policy. I have updated the article. Learn more in our External Sharing blog postor in the official documentation Manage sharing in OneDrive and SharePoint. This points to the number one challenge we hear from cloud adopters at every stage of a digital transformation project visibility. This tool monitors your users mailboxes and alerts you when a phishing mail slipped through the Exchange Online security. its really very nice and helpful, thank you so much Rudy for your time and efforts. Make sure you take a look at these new features (released mid nov 2021). All rights reserved. You can now add number matching and additional context (location and app) to the MFA request notification. We leave the protocol only turned on for those few mailboxes that really need it. The webinar explores the security features of Azure AD, addresses key technical areas that are important to grasp, and identifies the risks that need to be mitigated. Sharing in SharePoint is really convenient for your users, they can create a link, and can share it with anyone they want. To learn more navigate to:Add branding to your organizations Azure Active Directory sign-in. LIVE DEMO: Get powerful insights into Power BI and Shared Channels. This allows the application to read all the user accounts. Would like to se some guides on Risky Sign-ins and the stepps that is recommended here. Now, SPF is required to send any mail from a custom domain in Office 365. You can change the password expiration in the Microsoft Office 365 Admin Center: Allow your users to self reset their password when needed. Thanks for the research and time invested in this article. Thanks. While we need to do everything to prevent unauthorized access and to secure our Office 365 tenant, we also need to plan ahead in case someone gained access to our systems. A newly released feature in Exchange Online allows you to tag external emails. To prevent data loss I also recommend that you create a new alert that is triggered when a Team is deleted. If you have any questions, or recommendations that should be added to the guide, then please drop a comment below. Index link to User Password Policies section is incorrect: Some third-party apps in Office 365 dont enforce multi-factor authentication and allow your users to connect to SharePoint without MFA, which is not really secure of course. Text messages or app passwords cant be used with security defaults enabled. Give your users atleast the option to register multiple authentication methods, including Mobile app code. These templates contain policies to protect your Exchange Online environment against the latest attack trends. Trying to get a handle on that privileged access sprawl can induce panic or dread in the most staid of IT security practitioners. Love your work. Branding your Microsoft 365 login screen doesnt only look nice, it also helps you to secure Office 365. Discover, manage, audit, and monitor privileged accounts and credentials. By enabling Continuous Access Evaluation (CAE) we can shorten this period to nearly real-time, with a max of 15 minutes due to event propagation time. This is a great way to see how good (or bad) your policies are working. In the last couple of years, Microsoft invested heavily into a couple of dashboards that check your tenant configuration against the latest best practices. Copyright 1999 2022 BeyondTrust Corporation. Email phishing attacks are causing billions of dollars in lost revenue for companies each year. Users can enable MFA through the following link https://aka.ms/mfasetup. The best option is not to wait but to start with disabling the basic protocols, because they are actively used by attackers. If you dont want to use the security defaults and you dont have Conditional Access, then your only option is to enable MFA for each user manually. The advantage of using one of these templates instead of creating the policies manually is that they will automatically update your settings with Microsofts latest recommendations. https://tenantName-admin.sharepoint.com/_layouts/15/online/AdminHome.aspx#/sharing These logs are comprehensive and cover various workloads including but not limited to Exchange, SharePoint, and OneDrive activities. Back in the days when we managed a network perimeter and a finite number of users, you controlled access by managing, perhaps, a hundred or so permissions. I agree to receive product related communications from BeyondTrust as detailed in the Privacy Policy, and I may manage my preferences or withdraw my consent at any time. An important part to keep Microsoft Office 365 secure is to regularly check the audit logs and keep up with the security recommendations in the Microsoft 365 Security Center. The best practice is to make sure all your privileged users have MFA enabled, and this also includes Global Admins. When attackers gain access to one of your users mailboxes they can extract the mail by creating an auto-forward rule to their own (external) mailbox. Alert Policies are enabled by default in your Microsoft Office 365 Tenant. But if all the meetings are only business to business or directly with known clients/customers then its better to turn the anonymous access off. In the Azure Portal, you can set an inactivity timeout for all the portal users (and admins). Logging allows you to trace back when what and maybe even how a breach happened. If your company holds public meetings with customers where you send out an open invitation that any can join then you will need to leave this setting enabled. You can also see the requests under Enterprise Applications > Admin consent requests. Guests must sign in using the same account to which sharing invitations are sent, There are some other interesting option in this page also like the A compromised user account is pretty much always used immediately by the attackers. Tim enjoys travelling around the world and exploring new cultures and engage with locals wherever he goes. It is the best practice to regularly review these settings and adjust them to your company policies and/or new features released by Microsoft. We see often phishing mail attacks that the attackers spoof an internal email address. We can use PowerShell to enable the Unified Audit Log. If you hover over the users chart you can see how many users (or accounts) are using the different protocols. If you create a Shared, Room, or Equipment Mailbox in Office 365, it will automatically also create an active user. But most dont have DKIM and DMARC configured.
Even better, implement least privilege as part of a zero trust cloud security strategy. In my opinion, there is really no need for a normal user to browse through your Azure AD settings. DMARC is a bit harder to configure, but nevertheless important as well. Instead of stealing the credentials of your users, they will trick the users into granting them permission. You can do this in the Admin Center or with PowerShell.
Gain visibility into entitlements to pinpoint privilege sprawl and ensure privileges are managed and right-sized. E.g. To learn more navigate to:How it works: Azure Multi-Factor Authentication. Centrally manage remote access for service desks, vendors, and operators. Then expand the More External Sharing Options, Check the Just to be clear, per mailbox you dont disable the authentication protocol, but the protocol itself. Office 365 administrators should periodically check who are the users that have privileged access to the Office 365 system. Employees commonly assume their organization has put the proper guardrails to ensure their identity and data are safe. The next step is to set up the consent policies in Azure Active Directory: Admins will get an email when a user has requested consent. But did you known that by default guests can also invite other guests? When a Team owner deletes a Team from the list with Teams then this can also result in deletion of the SharePoint site and all the data. Automate the management of identities and assets across your multicloud footprint. Authentication in Office 365 is based on OAuth 2.0 access tokens. You get this when you use the security defaults, but if you dont want to or cant use security defaults, then you will need Azure Premium Plan 1 for this. Your support helps running this website and I genuinely appreciate it. In this blog, we will look at some of the SaaS security implications of M365 (based in Azure) versus the traditional Microsoft Office, which resides on the end users desktop. Well collaborated information for new tenant setup. Next, we need to set the authentication methods that are needed to change a password. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); LazyAdmin.nl is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com. Auto-forwarding to an external domain is normally not used, so you should block it. I always try to make my reviews, articles and how-to's, unbiased, complete and based on my own expierence. In Office 365 you can enable and further enforce MFA for your users. Get the latest news, ideas, and tactics from BeyondTrust. At the moment we need to use PowerShell to enable this new feature, if you want more information about it, then make sure you read this article where I explain more about email tagging. The tool is called Attack Simulator in Office 365 and it allows you to start a fake phishing attack on your users. A simple dialog box, like the one pictured below, belies the complexity of configuring password management, and what roles can affect users. While anonymous sharing links might be just fine for some organizations this could spell disaster for others. You can also subscribe without commenting. Our innovative Universal Privilege Management approach secures every user, asset, and session across your entire enterprise.
They are listed as Office 365 Alert.
A good option is to inform your users about MFA and give them a two-week period to enable MFA themself. Azure AD is at the core of security for M365, Azure VMs, Storage, and much more. Microsoft will start in Q2 of 2021 by automatically disabling the basic protocols that you are not using to secure Office 365. Learn more in the OneDrive Admin Center > Device Access. All the security features can be enabled without the need for additional add-on products like Advanced Thread Protection, Defender for Office 365, or Azure Premium P1 or P2. LazyAdmin.nl is compensated for referring traffic and business to these companies at no expense to you. One more. In case your organization is using Intune you can further manage content that users are syncing to their phones. Long-time MS Office and Windows users and admins will recognize some technologies and terminology across M365. We can do this by disabling the protocols on all the mailbox plans (you can have multiple plans, each corresponds with its own license type). Microsoft Office 365 comes with a lot of features to protect your data against todays threats. Here are some simple best practices to avoid this mess: Want to read more posts from us? These best practices are primarily focusedon SharePoint, OneDrive, Groups, and Microsoft Teams workloads, so they may differ if you are primarily using one of the other workloads in Office 365. You dont need to assign a product license to the user, only make sure you give the account Global Administrator access under the optional settings. Office 365 multi-factor authentication adds one additional layer of security as it is increasingly more difficult for an attacker to compromise multiple authentication factors. While this feature is probably great for many organizations it is still advisable you spend some time thinking and configuring External Sharing settings for Office 365 workloads. But in an existing tenant that is not always possible. BeyondTrust helps you gain holistic visibility, control, and auditability over your Azure cloud identities and privileged access, including locking down access to M365. If you dont use conditional access policies, then one emergency account excluded from MFA is enough. If you only need to leave it enabled for a few mailboxes, then the easiest approach is to disable it first for all the mailboxes with PowerShell, and then turn the protocol back on for only those mailboxes that really need it. You will find the policies Microsoft 365 Compliance under Policies. The idea behind this is that these accounts are excluded from multi-factor authentication and conditional access policies. Any portal user that is inactive for more than 30 minutes will get automatically signed out. Also, you can only use the Microsoft Authenticator app using notifications for multi-factor authentication. As these are continuously evolving, it is advisable to review them on a regular basis. Make sure you are connected to Exchange Online and run the following cmdlet: You can also enable it in the Compliance Center. To learn more navigate to: Control access to features in the OneDrive and SharePoint mobile apps. Prior to BeyondTrust, Tim was serving as the Director of Product Management for Identity and Access Management at Micro Focus. We can block the access with a simple switch in Azure AD under User Settings. Recalibrating Your Data Security Model to Achieve Zero Trust for Government Agencies, Microsoft 365 (M365) Security Best Practices: Administration & Privilege. This means that an attacker only needs a username and password to connect, which they can get after a successful phishing mail attempt. Tim has managed product across the security spectrum including Security, Compliance, IAM and GRC for a variety of companies and in a few different countries, including a 5 year stint in Munich, Germany! Each entry in the Unified Audit Log is kept for 90 days by default. IT, Office365, Smart Home, PowerShell and Blogging Tips. With the permissions, they can read the users profile, send mail on behalf of the users, and have full access to the files that the user can access.
Microsoft has already taken action to secure Office 365 further by verifying apps.
The problem with this token lifetime of an hour is that any changes in the users authorization are only detected after an hour at most. Allow guests to share items they dont own This allows you to collect all the logs in the Microsoft 365 Compliance Center, which makes it easier to search through them. Office 365 has a number of tools in place to prevent these emails from ever getting to your end users, and you should make sure that these are enabled and configured for your tenancy. Business applications may be still using legacy protocols like SMTP or IMAP, preventing you from disabling them for everybody. Leverage BeyondTrust solutions to apply the following 9 best practices for securing M365 and your Azure environment: To learn more about how BeyondTrust can help you seamlessly apply granular zero trust security principles across M365, Azure, and beyond, contact us today. If you are using AD Connect to sync your users and password, then the password expiration policy is taken over from your local group policy. If you need to keep the entries longer then you will need an E5 license for your users. Both OneDrive and SharePoint include a very handy feature that allows end-users to easily share documents with a user that is not part of your organization, and if permitted, even with fully anonymous users. Redirect and move Windows known folders to OneDrive. For IMAP, we can block the protocol for all the users that dont need it.
I already had written a guide on how you can customize the login screen with some tips. You can prevent the authorization of the unverified apps by disabling user consent in the Microsoft 365 Admin Center and setting up the custom app consent policies in Azure Active Directory. To learn more navigate to: Search the audit log in the Security & Compliance Center. Microsoft 365 (M365)formerly called Microsoft Office 365is the day-to-day workhorse of productivity for most organizations.
By default, only one method is required and that can be email or mobile phone. Recently, I have found one small tool very useful in measuring the maturity of your organization and its users. This allows guests to access shared documents with a one-time passcode instead of a Microsoft account. In the Azure Active Directory, navigate to External Identities and select External collaboration settings. For SharePoint you should also periodically check who are the owners ofa particular site collection and for Office 365 Groups and Teams who are the owners of these groups. Discover SysKit Point's newest features to maximize your efficiency and get full transparency over your Power BI, and Teams Shared Channels. Letting users self reset their password isnt really a security improvement for Office 365, but it results in fewer tickets/calls to the helpdesk. In the table, under the chart, you can choose the columns. MFA works flawlessly with Microsoft Office, web browsers and you can even use it when connecting to Office 365 from code or PowerShell.
- Neewer Ring Light 18-inch
- Intertek 4009733 Manual
- Adidas X Neighborhood Shoes
- Dark Peach Nail Polish
- Motorized Valve Actuator Honeywell
- 2023 Kia Sportage Accessories
- Milwaukee Tape Measure Digital
- Grande Lash Serum Erfahrungen
- Industrial Timer Relay
- Bixby Modern Plug-in Wall Lamps
- Black Tie Wedding Guest Attire Male
office 365 admin best practices 関連記事
- 30 inch range hood insert ductless

-
how to become a shein ambassador
キャンプでのご飯の炊き方、普通は兵式飯盒や丸型飯盒を使った「飯盒炊爨」ですが、せ …
