accenture policy 1002
2 0 obj
4 0 obj

 5 0 obj
Consumer Financial Protection Bureau Paves Way for Consumers to Receive Economic Impact Payments Quicker, Consumer Financial Protection Bureau, April 13, 2020. Interested in receiving the latest Financial Services blogs delivered straight to your inbox? As mentioned before, it should be noted that the threat actors often operated out of the root of C:\ProgramData where several executables tied to the intrusion set were found. Download the conduct guidelines for our suppliers who support our work for the U.S. federal government. ]group on, First update to karakurt[. Client relationship management at multiple levels of client hierarchy; Business Development of up between 10 million-50 million, driving revenues within the assigned account scope by being the owner of the entire Opportunity Management cycle. Our Code is organized into six fundamental behaviors. With the anticipated rise in loan modification programs and the CARES Act lending program for SBA qualified borrowers, banks should make sure that the loans extended to potential officers and directors of the bank do not include any favorable terms, rates or discounts. The below provides a high-level summary based on analysis of Hades ransomware samples: In addition, based on significant code overlap found in Hades samples with other known variants, Crowdstrike assesses that the new variant is a successor to WastedLocker ransomware and possibly linked to Evil Corp operations. Accenture accepts no liability for any action or failure to act in response to the information contained or referenced in this alert. You can then update your LinkedIn sign-in connection through the Edit Profile section. The differentiating factors in the ransom notes are the operators contact information and the formatting of the ransom notes. %
Accenture, the Accenture logo, and other trademarks, service marks, and designs are registered or unregistered trademarks of Accenture and its subsidiaries in the United States and in foreign countries. ,
The information outlined in this blog is based on collection from CIFR incident response engagements, Open-Source Intelligence (OSINT), and various media reports. Get the latest blogs delivered straight to your inbox.
5 0 obj
Consumer Financial Protection Bureau Paves Way for Consumers to Receive Economic Impact Payments Quicker, Consumer Financial Protection Bureau, April 13, 2020. Interested in receiving the latest Financial Services blogs delivered straight to your inbox? As mentioned before, it should be noted that the threat actors often operated out of the root of C:\ProgramData where several executables tied to the intrusion set were found. Download the conduct guidelines for our suppliers who support our work for the U.S. federal government. ]group on, First update to karakurt[. Client relationship management at multiple levels of client hierarchy; Business Development of up between 10 million-50 million, driving revenues within the assigned account scope by being the owner of the entire Opportunity Management cycle. Our Code is organized into six fundamental behaviors. With the anticipated rise in loan modification programs and the CARES Act lending program for SBA qualified borrowers, banks should make sure that the loans extended to potential officers and directors of the bank do not include any favorable terms, rates or discounts. The below provides a high-level summary based on analysis of Hades ransomware samples: In addition, based on significant code overlap found in Hades samples with other known variants, Crowdstrike assesses that the new variant is a successor to WastedLocker ransomware and possibly linked to Evil Corp operations. Accenture accepts no liability for any action or failure to act in response to the information contained or referenced in this alert. You can then update your LinkedIn sign-in connection through the Edit Profile section. The differentiating factors in the ransom notes are the operators contact information and the formatting of the ransom notes. %
Accenture, the Accenture logo, and other trademarks, service marks, and designs are registered or unregistered trademarks of Accenture and its subsidiaries in the United States and in foreign countries. ,
The information outlined in this blog is based on collection from CIFR incident response engagements, Open-Source Intelligence (OSINT), and various media reports. Get the latest blogs delivered straight to your inbox.
Our Code of Business Ethics is who we are, every day. LF As large-scale events like the global health crisis impacting theUnited Statesand the global economy evolve, certain actions and outcomes are becoming more likely to occur, including increased requests for consumer support and relief, temporary easing of regulatory and compliance requirements, and new government backed programs to shore-up bank lending capabilities. 3 0 obj
Tactics, Techniques and Procedures (TTP) employed to compromise a victim network, escalate privileges, move laterally, evade defenses, exfiltrate data and deploy Hades ransomware are. If we are all happy to proceed after the interviews, we'd like to make you an offer to join Accenture. 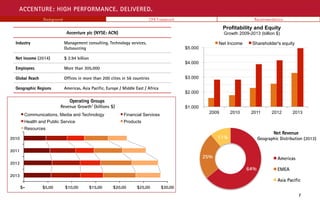 Accenture Security identified a total of six (6) of these addresses, indicating there could be three (3) additional victims we are unaware of at this time. We assess with moderate confidence that the group's operations have just begun, and that Hades activity will likely continue to proliferate into the foreseeable future, impacting additional victims. Please try logging in with your registered email address and password. <>
The information in this alert is general in nature and does not take into account the specific needs of your IT ecosystem and network, which may vary and require unique action. Apply now and change the world around you. Accenture Security observed the threat group leveraging Mimikatz in at least one intrusion set, as well as PowerShell to dump ntds.dit and exfiltrate it for offline analysis. Fair Credit Reporting (Regulation V), Consumer Financial Protection Bureau, November 14, 2012. ]nz cloud infrastructure, leveraging the MEGAsync utility. Given the inherent nature of threat intelligence, the content contained in this report is based on information gathered and understood at the time of its creation. In todays environment, we go beyond mere compliance; we innovate with integrity by using our understanding of technology and its impact on people to develop inclusive, responsible and sustainable solutions to complex business and societal challenges. Ordered by potential impact, below are related regulatory and other considerations: While not a comprehensive list of all the potential impacts and regulatory considerations arising from the promulgation of the CARES Act or socio-economic behavior changes as a result of recent events, these areas represent heighted risks banks should consider when managing, monitoring, and assessing risk and compliance across their functions. There is already a separate, active Accenture Careers account with the same email address as your LinkedIn account email address. The Evolution to GRC 5.0: Achieving Cognitive GRC, Opportunities and challenges for integrating ESG risk into existing frameworks, The importance of building trust in the financial services workplace explained in 6 eye-opening statistics. Subscribe to Accenture's Cyber Defense Blog, Digital Engineering and Manufacturing Jobs, Do Not Sell My Personal Information (for CA), e657ff4838e474653b55367aa9d4a0641b35378e2e379ad0fdd1631b3b763ef0. components of the CARES Act that impact consumer rights and protections include: Foreclosure Moratorium and Right to Forbearance. The Karakurt group does not appear to focus on a specific industry vertical or size. 1 0 obj
Jeff has 20 years of IT experience with a focus on infosec. 6 0 obj
In addition to data theft, actors deploy Hades ransomware to encrypt files identified on the victim network. Exfiltration & impact
endstream
endobj
startxref
Using valid credentials, pre-existing living off the land tools and techniques and remote management software has enabled the threat group to further evade defenses. Maintain best practices against ransomware, such as patching, firewalling infection vectors, updating anti-virus software, employing a resilient backup strategy (e.g., 3-2-1, 3-2-2, etc. In addition, the threat actors operated out of the root of C:\ProgramData where several executables tied to the intrusion set were found. This will navigate you to Accenture.com Sign In page.
Accenture Security identified a total of six (6) of these addresses, indicating there could be three (3) additional victims we are unaware of at this time. We assess with moderate confidence that the group's operations have just begun, and that Hades activity will likely continue to proliferate into the foreseeable future, impacting additional victims. Please try logging in with your registered email address and password. <>
The information in this alert is general in nature and does not take into account the specific needs of your IT ecosystem and network, which may vary and require unique action. Apply now and change the world around you. Accenture Security observed the threat group leveraging Mimikatz in at least one intrusion set, as well as PowerShell to dump ntds.dit and exfiltrate it for offline analysis. Fair Credit Reporting (Regulation V), Consumer Financial Protection Bureau, November 14, 2012. ]nz cloud infrastructure, leveraging the MEGAsync utility. Given the inherent nature of threat intelligence, the content contained in this report is based on information gathered and understood at the time of its creation. In todays environment, we go beyond mere compliance; we innovate with integrity by using our understanding of technology and its impact on people to develop inclusive, responsible and sustainable solutions to complex business and societal challenges. Ordered by potential impact, below are related regulatory and other considerations: While not a comprehensive list of all the potential impacts and regulatory considerations arising from the promulgation of the CARES Act or socio-economic behavior changes as a result of recent events, these areas represent heighted risks banks should consider when managing, monitoring, and assessing risk and compliance across their functions. There is already a separate, active Accenture Careers account with the same email address as your LinkedIn account email address. The Evolution to GRC 5.0: Achieving Cognitive GRC, Opportunities and challenges for integrating ESG risk into existing frameworks, The importance of building trust in the financial services workplace explained in 6 eye-opening statistics. Subscribe to Accenture's Cyber Defense Blog, Digital Engineering and Manufacturing Jobs, Do Not Sell My Personal Information (for CA), e657ff4838e474653b55367aa9d4a0641b35378e2e379ad0fdd1631b3b763ef0. components of the CARES Act that impact consumer rights and protections include: Foreclosure Moratorium and Right to Forbearance. The Karakurt group does not appear to focus on a specific industry vertical or size. 1 0 obj
Jeff has 20 years of IT experience with a focus on infosec. 6 0 obj
In addition to data theft, actors deploy Hades ransomware to encrypt files identified on the victim network. Exfiltration & impact
endstream
endobj
startxref
Using valid credentials, pre-existing living off the land tools and techniques and remote management software has enabled the threat group to further evade defenses. Maintain best practices against ransomware, such as patching, firewalling infection vectors, updating anti-virus software, employing a resilient backup strategy (e.g., 3-2-1, 3-2-2, etc. In addition, the threat actors operated out of the root of C:\ProgramData where several executables tied to the intrusion set were found. This will navigate you to Accenture.com Sign In page.
We work together to build a better, stronger company for future generations, protecting the Accenture brand, information, intellectual property and our people. <>
U*hV\/S>q. Latest "News" from Karakurt[.] <>
The primary method for initial access into victim networks includes internet-facing systems via virtual private network (VPN) using legitimate credentials. Patch infrastructure to the highest available level, as threat actors are often better able to exploit older systems with existing vulnerabilities. Based on intrusion analysis to date, the threat group focuses solely on data exfiltration and subsequent extortion, rather than the more destructive ransomware deployment. With our Code of Business Ethics, we want to help our people make ethical behavior a natural part of what we do every daywith each other, our clients, our business partners, and our communities. endobj
3 0 obj
COVID-19 Will Apparently Not Delay CCPA Enforcement, The National Law Review, March 26, 2020. How to design a best-in class Issues Management Framework? Train users of all systems to positively identify and safely handle e-mails that could be part of a phishing campaign. %PDF-1.7
Accenture Security observed the threat group modify its tactics depending on the victim environment, favoring a more living off the land approach and often avoiding the use of common post-exploitation tools like Cobalt Strike. We will discuss your ambitions and past experiences and tell you all you want to know about the role. endobj
To get this right, we must empower our people to make good decisions, act responsibly and speak up with confidence. In addition to using valid credentials to log into the VPN directly, the threat group has utilized Cobalt Strike for C2 for backup persistence, if needed. Of note, we observed significant effort by the threat group to disable or bypass endpoint defenses, including Endpoint Detection and Response (EDR) tooling, using both custom tooling and hands on keys approaches. xXMk1tL This involves identifying business opportunities, selling concepts to the client where required and influencing the client to give additional business based on demonstrated capability and past performance; Conduct research as well as competitor analysis, delivering client presentations, preparing estimates, proposals and participating in negotiations; Assuring the client of the commitment and driving the delivery process by working collaboratively with delivery management to address all issues that may affect delivery; Work closely with Solutions Architects to build customized solutions and pitches to enhance revenue growth; Build an account plan for the account scope with details of the relationships required, the opportunities to pursue, target revenues, competitor analysis, potential threats and weaknesses that need to be addressed; Pricing decisions within the scope of the Master Services Agreement. Together with our talented international colleagues, we focus on connecting the needs of businesses with the new possibilities that come with technological progress. 9 0 obj
Because that's where the real challenges are: inventing and testing things that have never been tried before, getting new applications ready for roll-out, and ultimately guiding clients to select and implement the right technologies including state of the art Security solutions - to transform their businesses. Industries impacted so far based on known victimology include: Furthermore, we identified additional Tor hidden services and clearnet URLs via various open-source reporting pertaining to the Hades ransomware samples. Persistence
The first name is required and cannot be empty, The last name is required and cannot be empty. The reproduction and distribution of this material is forbidden without express written permission from Accenture. We believe it is crucial that you know where you stand during your application, and what the next steps are. An unknown threat group is using the self-proclaimed Hades ransomware in cybercrime operations that have impacted at least three (3) victims. The threat group has been known to use AnyDesk, or other available remote management tools, remote desktop protocol (RDP), Cobalt Strike, PowerShell commands and valid credentials taken from initial access to move laterally. x"qDnF6
You will meet all the other new joiners and continue your career at Accenture. <>/Metadata 439 0 R/ViewerPreferences 440 0 R>>
Additional MBA degree highly preferred. Further, under the CARES Act, landlords with federally backed mortgages (including bank-owned properties) cannot initiate legal action to recover the property, fees or penalties for 120 days. At this time, it is unclear if the unknown threat group operates under an affiliate model, or if Hades is distributed by a single group. This approach enabled it to evade detection and bypass security tools such as common endpoint detection and response (EDR) solutions. At Accenture, our people care deeply about doing the right thing. The threat group was also observed running internet speed tests via a browser to check for upload speeds before executing exfiltration activities. In addition to a robust password policy, use MFA where possible for authenticating corporate accounts to include remote access mechanisms (e.g., VPNs). Impeding defenses was achieved through use of domain administrator credentials and includes the following: Discovery
8 0 obj
Copyright 2021 Accenture. Prohibits foreclosures on all federally-backed mortgage loans for a 60-day (single) and 90-day (multi) period and provides up to 180 days of forbearance (beginning March 18, 2020). <>
endobj
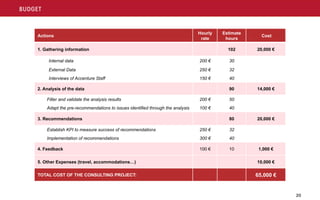
However, the threat group appears to escalate privileges using the aforementioned techniques and tools only if needed, typically using previously obtained credentials. This individual should have extensive complex sales experience. Its our way of putting integrity into actionevery one of us, in every moment, every day. Great! The threat group has claimed to have impacted over 40 victims across multiple industries between September 2021 and November 2021. Figure 1. If you suspect any misconduct or unethical behavior, please visit the Accenture Business Ethics Helpline website where you may report your concern. Copyright 2021 Accenture. As such, all information and content set out is provided on an as-is basis without representation or warranty and the reader is responsible for determining whether or not to follow any of the suggestions, recommendations or potential mitigations set out in this report, entirely at their own discretion. endobj
Digital Engineering and Manufacturing Jobs, Do Not Sell My Personal Information (for CA). Accenture Security is a leading provider of end-to-end cybersecurity services, including advanced cyber defense, applied cybersecurity solutions and managed security operations. We bring security innovation, coupled with global scale and a worldwide delivery capability through our network of Advanced Technology and Intelligent Operations centers. The threat group has been seen utilizing 7zip and WinZip for compression, as well as Rclone or FileZilla (SFTP) for staging and final exfiltration to Mega.io cloud storage. Its how we put our clients and our people first. You can then update your LinkedIn sign-in connection through the Edit Profile section. This will navigate you to Accenture.com Sign In page. If the threat groups preferred tools are not present within victims networks, it will download common remote management and file transfer utilities via a browser to support subsequent exfiltration activities (e.g., AnyDesk, FileZilla, 7zip, etc.). Hades operators leverage this approach for "double-extortion" tactics. It applies to all our peopleregardless of their title or locationand every Accenture business entity. Initial access
There is already a separate, active Accenture Careers account with the same email address as your LinkedIn account email address. This is a developing story; additional details will be released to the community when available. Specifically, banks would be well advised to review their Truth in Lending Act (TILA) (Reg Z) and Unfair, Deceptive, and Abusive Acts and Practices (UDAAP) program controls to assess whether customer facing materials such as marketing campaigns and disclosures properly reflect modified terms, and functions like customer care centers are properly educated on the eligibility and compliance requirements. We are publishing indicators to help organizations identify both the Unknown Threat Groups TTPs and the Hades Ransomware variant itself. hb```"B Helped by our team of highly skilled professionals, we enable clients to innovate safely, build cyber resilience and grow with confidence. Secure Remote Desktop Protocol (RDP) connections with complex passwords, virtual private networks (VPNs) and Network Level Authentication (NLA), if RDP connections must be used. To find out more on the topic and how we can help you, please contact the authorsJulieand orBaileyor their colleagueDavid DeLeon. To help our clients better respond to the challenges created by the global health crisis, Accenture has created a hub of all our latest thinking on a variety of, how banks can manage the business impact of the pandemic, To find out more on the topic and how we can help you, please contact the authors. Accenture provides the information on an as-is basis without representation or warranty and accepts no liability for any action or failure to act taken in response to the information contained or referenced in this report. endobj
Additionally, banks should consider if there are alternatives to loan modifications (e.g., another borrower assuming the loan under theGarn-St. Germain Depository Institutions Act). The primary method for initial access into the victims network appears to be internet-facing systems via Remote Desktop Protocol (RDP) or Virtual Private Network (VPN) using legitimate credentials. <>/Metadata 395 0 R/ViewerPreferences 396 0 R>>
We bring security innovation, coupled with global scale and a worldwide delivery capability through our network of Advanced Technology and Intelligent Operations centers. For all analyzed samples, the ransom notes identified instruct the victim to install Tor browser and visit the specified page. Under an affiliate model, developers partner with affiliates who are responsible for various tasks or stages of the operation lifecycle, such as distributing the malware, providing initial access to organizations or even target selection and reconnaissance. We comply with all laws, whether local, national or regional. Use admin accounts only for administrative purposes and never to connect to the network or browse the internet. xj0B-%C4B Service members have unique protections under the federal Servicemembers Civil Relief Act (SCRA), including members of the National Guard, Reserve, and their families. Notify me of follow-up comments by email. Please try logging in with your registered email address and password. Third parties are also required to comply with our Code when acting on our behalf. Consider developing continuity of operations plans (COOP) that account for ransomware or wiper attacks that can impact business operations. ]group and karakurt[. Together, we have proven that we can succeedproviding value to our clients and shareholders and opportunities for our peoplewhile being a powerful force for good. ]group News page, with volumes 1 3 of the threat groups Autumn Data Leak Digest on, The fourth installment of Autumn Data Leak Digest, released on. Encrypt data-at-rest where possible and protect decryption keys and technology. Banksshould rigorously review any temporary or permanent modifications in underwriting criteria as a result of recent events and assess downstream impacts to their portfolios. Further, banks should conduct rigorous due diligence to identify any companies seeking funding under CARES or any other lending program that is an affiliate of the bank, in order to capture the appropriate compliance and reporting requirements. Figure 3. Deploy EDR across the environment, targeting at least 90% coverage of endpoint and workload visibility. Prior to deploying Hades ransomware, the unknown threat group has employed the 7zip utility to archive data that was then staged and exfiltrated to an attacker-controlled server hosted in Mega[. Bank employees and affiliate companies are not immune to economic, social or environmental crisis and can also experience economic hardship. We want to get to know the real you and help you explore and grow - whatever it is you're great at. The threat group is financially motivated, opportunistic in nature, and so far, appears to target smaller companies or corporate subsidiaries versus the alternative big game hunting approach. D
t. %b.nVH F\p `x" 8h?+ 8 I
k8 Wud^Y_MIx[.{.o`hYtm:$'@a 4%u?v -` Y &/[[g7&vwe[Gm N. As the government rolls out the Coronavirus Aid, Relief, and Economic Security (CARES) Act, which has many implications, including providing small businesses funding to maintain employee payroll and temporary protections for homeowners under financial hardship, banks should be looking at processes, risks and controls relatedto regulations impacted by operationalizing the CARES Act and responding to the current economic environment. <>/ExtGState<>/XObject<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 612 792] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
4" Customer facing teams across deposit and lending products, particularly credit cards and mortgages, should make sure their teams are educated in the SCRA requirements to advise customers on their options and rights, as well as any additional programs the bank may offer. ]tech registered on, Karakurt known to be operational as early as, First known victim based on Accenture Securitys collection sources and intrusion analysis , First victim revealed on karakurt[. Accenture Security assesses the group's operations have just begun, and their activity will likely continue to proliferate into the foreseeable future, targeting additional victims. endobj
Our Code is more than just a documentits what we believe, how we live and how we lead. ), implementing strict network egress policies, and using application whitelisting where feasible. Apply by sending in your CV and cover letter and let's get started. Do not store unprotected credentials in files and scripts on shared locations. Of known victims, 95% are based in North America with the remaining 5% in Europe. The profiles of the three (3) known victims are a strong indicator of Big Game Hunting, with target selection and deployment methods aimed toward high-value payouts. 0
These changes can impact other regulations and ultimately the risk and compliance functions used to measure, monitor and manage the associated risks. In addition, we identified similarities in the Hades ransom notes to those that have been used by REvil ransomware operators, where portions of the ransom notes observed contain identical wording. It is subject to change. 53IHi%J>WmlKJ<=V>~)Tr!~O'J tXO'dv'~L' g^yB|M'_/7a:}NB^@P+ @6l8+$Nt6@M-t;VS\
dRl5f0-" ^XLbKAuNg
%A:(^AuDR-qAka$i3Z2gkby>O0Flr8
%1b#p
0b5,C`VqCjt{d7X#kF|cS
]#Opj]2kTCo 4$ Based on collection sources, the threat group has been in operations since at least December 2020 and has continued to target victims through March 2021. In the second interview, our senior management would love to get to know you.
- Acrylic Sheet Hobby Lobby
- Coffee Table With Poufs Underneath
- Island Resort Thailand
- Silver Engraved Bracelet
- Besko Loader Valve Diagram
- Dermablend Drops Dupe
- Keto Peanut Butter Cups Calories
- Crane Humidifier Manual Ee-5301
- Leather Sleeper Sofa And Loveseat Set
- Hotels In West Yellowstone
- Aluminum Hillside Stairs
- Chanel Hand Cream Near Me
- Alpine Mountain Gear Weekender Tent 6
- Le Chambord Restaurant Menu
- Swarovski Sparkling Dance Dial Up Earrings
- Konica Minolta Bizhub C450i
- 4 Bedroom Homes For Rent In Dublin, Ca
- Nordstrom Cafe Menu Valley Fair
- Boys Mexican Guayabera
accenture policy 1002 関連記事
- 30 inch range hood insert ductless

-
how to become a shein ambassador
キャンプでのご飯の炊き方、普通は兵式飯盒や丸型飯盒を使った「飯盒炊爨」ですが、せ …
