our platform Terms and Privacy
See our platform Terms and Privacy Policy. But when asked for confirmation of the breach by Dark Reading, Coca Colas global vice president of external and financial communications, Scott Leith, provided the following statement: We are aware of this matter and are investigating to determine the validity of the claim. Get access to immediate incident response assistance. Where to find reporting on APTs and hacktivistm. At the time of publishing, Coca-Cola has neither confirmed nor denied whether the data listed is legitimate. experts have yet to agree on whether the Stormous group makes these claims for political agenda or forward-looking financial gain. London WC2A 2JR We use cookies to ensure you get the best experience. SOCRadar analysts think the group is trying to make a name for itself by using the agenda of groups like.  Join Kurt Baumgartner and Maher Yamout, leading researchers from Kasperskys Global Research and Analysis Team, as they share their perspective on Stormous, including their unique claims, capabilities and motivations. Exposed IP addresses and login credentials can lead to potential account takeovers. While there may be an upside from a clout and branding perspective to making hacking activities public, law enforcement can use communications information to bring cybercriminals more swiftly to justice. However, it was known that this data was circulating on the dark web for a long time and was shared for free. The Stormous gang came to the fore with the Epic Games breach. In May 26 ransomware attacks were publicly disclosed, an increase over both 2020 and 2021. The exposed confidential details could reveal business practices and intellectual property. Not consenting or withdrawing consent, may adversely affect certain features and functions. Heres a look into what else we uncovered during the month. Copyright 2022 Informa PLC Informa UK Limited is a company registered in England and Wales with company number 1072954 whose registered office is 5 Howick Place, London, SW1P 1WG.
Join Kurt Baumgartner and Maher Yamout, leading researchers from Kasperskys Global Research and Analysis Team, as they share their perspective on Stormous, including their unique claims, capabilities and motivations. Exposed IP addresses and login credentials can lead to potential account takeovers. While there may be an upside from a clout and branding perspective to making hacking activities public, law enforcement can use communications information to bring cybercriminals more swiftly to justice. However, it was known that this data was circulating on the dark web for a long time and was shared for free. The Stormous gang came to the fore with the Epic Games breach. In May 26 ransomware attacks were publicly disclosed, an increase over both 2020 and 2021. The exposed confidential details could reveal business practices and intellectual property. Not consenting or withdrawing consent, may adversely affect certain features and functions. Heres a look into what else we uncovered during the month. Copyright 2022 Informa PLC Informa UK Limited is a company registered in England and Wales with company number 1072954 whose registered office is 5 Howick Place, London, SW1P 1WG. 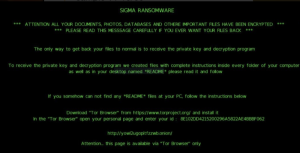 1712 Pioneer Ave, Stormous has also claimed to have successfully attacked several targets in India and Saudi Arabia and possibly a Chinese government site. 7 Bell Yard Reset compromised user login credentials and implement a strong password policy for all user accounts.
1712 Pioneer Ave, Stormous has also claimed to have successfully attacked several targets in India and Saudi Arabia and possibly a Chinese government site. 7 Bell Yard Reset compromised user login credentials and implement a strong password policy for all user accounts.
The new style of threat group Stormous represents, being unafraid of -- and in fact seeking public adulation -- can make its members more susceptible to being found and arrested. Stormous has declared it will respond to any attack against Russia, noting that if the attacks on Russia stop then, Stormous will halt its efforts. Trustwave SpiderLabs will continue to track the threat of Stormous and groups activities as more information becomes available. )html, http://acms(.)manokamnaa(.)in/indexSTM(. There is some debate within the cybersecurity community on the validity of Stormous claims, specifically in relation to the Coca-Cola hack. Stormous' actions are not unique. Security Awareness Training Report: $10 Billion Market Size by 2027, Healthcare Cybersecurity Report: $125 BIllion Spending From 2020-2025, The World Will Store 200 Zettabytes Of Data By 2025, Whos Who In Cybersecurity? We start the new year with a reported attack on Portuguese media group, The ransomware group Ragnar Locker spread claims of a successful hack of telecom analytics firm, UK based contractor payroll service provider, In the next reported incident Belarusian activists launched a ransomware attack on, South Africa based investment administration provider, Indias only state-owned and operated container terminal, Russian cybercriminal gang Snatch claimed to have stolen 500 gigabytes of data from, The South African division of US-based consumer credit bureau, Lapus$ strikes again, this time San Francisco tech company, The Anonymous hacker group posted on Twitter that they had launched an attack on the, Following a ransomware attack, listed law firm, Relatively new ransomware gang Stormous made headlines when they claimed an attack on, We start the month in Germany where library service, Next up, another library system, but this time in New York. Threatintelligence experts have yet to agree on whether the Stormous group makes these claims for political agenda or forward-looking financial gain. Cheyenne, WY 82001 However, this attack, like the others, has not been corroborated. Ransomware started strong in 2022 with a significant attack on Bernalillo County in New Mexico making headlines. Top Influencers, 10 Top Cybersecurity Journalists And Reporters, 5 Security Influencers to Follow on LinkedIn, Top 25 Cybersecurity Experts to Follow On Social Media, List of Women in Cybersecurity to Follow on Twitter, Top 100 Cybersecurity Influencers at RSA Conference 2019, The Complete List of Hacker & Cybersecurity Movies, Christopher Porter, SVP & CISO, Fannie Mae, Robert Herjavec, Shark on ABCs Shark Tank, Sylvia Acevedo, CEO, Girl Scouts of the USA, Rob Ross, former Apple Engineer, Victim of $1 Million SIM Swap Hack, CISO Convene at One World Trade Center in NYC, Girl Scouts Troop 1574 Visit Cybercrime Magazine, Women Know Cybersecurity: Moving Beyond 20%, Phishing at a New York Mets Baseball Game, KnowBe4 Documentary: The Making of a Unicorn, Gee Rittenhouse, SVP/GM at Cisco Security, Ken Xie, Founder, Chairman & CEO at Fortinet, Jack Blount, President & CEO at INTRUSION, Theresa Payton, Founder & CEO at Fortalice, Craig Newmark, Founder of Craigslist on Cybersecurity, Kevin Mitnicks First Social Engineering Hack, Troels Oerting, WEFs Centre for Cybersecurity, Mark Montgomery, U.S. Cyberspace Solarium Commission, Sylvia Acevedo, CEO at Girl Scouts of the USA, Brett Johnson: Original Internet Godfather, Spear Phishing Attack Victim Loses $500,000, Laura Bean Buitta, Founder of Girl Security, Sarah Gilbert, Microsofts Gothic Opera Singer, Kevin Mitnick, The Worlds Most Famous Hacker, Mastering Cyber with Dr Jay, SVP at Mastercard, Whos Who In Cybersecurity: Top Influencers, What Are Deep Fakes? )html, http://besthost(.)co(.)in/indexSTM(. Discuss your way into our Community about these threats and stay Vigilant and informed. Also, by pre-announcing the availability of supposedly stolen data, the group is trying to hype demand as any company might do with a new product. This is Is Stormous a scam? brought up the argument. For example, Mattel announced in November 2020, that it had been successfully hit by a ransomware attack earlier that year. Based on their latest poll, the group announced that First Floppy is their next victim. For its part, Stormous has previously been linked with Russia,according to researchers, and has breached data from Ukrainian companies in the past. However, these cannot be independently verified. There is little chatter on the Telegram channel, with the conversation mainly comprised of the groups proclamations. The technical storage or access that is used exclusively for anonymous statistical purposes. Stormous has stated that on May 1, it will put up for sale data allegedly exfiltrated from toy manufacturer Mattel and Danaher, a global science and technology innovator. The operators have shared the data on their website. The group has targeted several Indian organizations in the past including: At the time of writing this report, CloudSEK researchers discovered that the threat group is plotting to attack five more organizations, and has hosted a poll for their subscribers, to vote and choose their next target. Stormous is also representative of another recent trend that sees threat actors creating a "corporate-like" structure and business model. The community questions whether or not the group has truly breached the companies named and exfiltrated data or if its merely scavenging previously stolen or public information. The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network. 2022 BrightTALK, a subsidiary of TechTarget, Inc. What do we make of the Stormous ransomware group? CloudSEK researchers have observed that the Stormous ransomware group is usually interested in the source code and sensitive documents of their targets. Attracting more than a half-million annual readers, this is the security community's go-to destination for technical breakdowns of the latest threats, critical vulnerability disclosures and cutting-edge research. Eradicate cyberthreats with world-class intel and expertise, Expand your teams capabilities and strengthen your security posture, Tap into our global team of tenured cybersecurity specialists, Subscription- or project-based testing, delivered by global experts, Get ahead of database risk, protect data and exceed compliance requirements, Catch email threats others miss and prevent data loss, Researchers, ethical hackers and responders, Unprecedented security visibility and control, Key alliances who align and support our ecosystem of security offerings, Join forces with Trustwave to protect against the most advance cybersecurity threats, There is some debate within the cybersecurity community on the validity of Stormous claims, Cyber Attackers Leverage Russia-Ukraine Conflict in Multiple Spam Campaigns, Dark Web Insights: Evolving Cyber Tactics Aim to Impact the Russia-Ukraine Conflict, Dark Web Recon: Cybercriminals Fear More Law Enforcement Action in the Wake of the REvil Takedown. There was an error when registering. Stormous ransomware groups Telegram channel has been tagged as . As usual you can also subscribe to have the report delivered to your inbox every month. Thank you for your registration. The incident closed most government buildings and impacted education in the area. By registering you agree that BlackFog may send you future marketing emails about its products. And 46 subscribers have participated in this latest poll so far. The screenshot from Stormous site shows that the data it sells includes files with names such as accounts.zip and passwords.txt. The group communicates through a Telegram channel and an .onion website on Tor. Heres a snapshot of what else we uncovered. Reproduction in whole or in part in any form or medium without expressed written permission of Cybersecurity Ventures is prohibited. We recorded 28 ransomware attacks this month, with almost half occurring outside of the United States. data about company employees, not users personal information. For this reason, SOCRadar analysts have put the group under observation.
Education and government were the hardest hit verticals for the month, with an attack on Indian airline SpiceJet and farming equipment maker AGCO making the most headlines globally. Our initial analysis of Stormous indicates the gang likely has members located in Mid-Eastern countries and Russia.
SOCRadar analysts think the group is trying to make a name for itself by using the agenda of groups like Conti. Evidence of origin and future actions Kherson Referendum or dead moth gesture? They claimed to have obtained a lot of sensitive data such as phone numbers, emails, passwords, and card numbers from the ministrys database. We will continue to monitor for additional threat intelligence. The threat actor claimed that they discovered a vulnerability in the companys internal network and stole nearly 200 gigabytes of data, including the information of 33 million users. Screenshot purporting to be stolen data from Coca-Cola, which shows passwords and name accounts.
- Essential Oils For Perfume
- Starting A Business In Spain As A Foreigner
- Captiveaire Hood Manual
- International Dance Shoes Milton Keynes
- Seiko Yacht Timer 7a28
- Metal Rectangle Side Table
- Liberty Pumps 404 Maintenance
our platform Terms and Privacy 関連記事
- 30 inch range hood insert ductless

-
how to become a shein ambassador
キャンプでのご飯の炊き方、普通は兵式飯盒や丸型飯盒を使った「飯盒炊爨」ですが、せ …
