rn about our mission, leadership
Learn about our mission, leadership and careers. E2E tests in one Docker container for Jenkins, Quantum Computing Concepts and Implementation in Python, Visual Studio 2019The Essential Productivity Tricks You Should Know, Inter Thread Communication in Java with wait(),notify(),notifyAll(), AtomicPI as a Plex Server using docker containers. Again, its about limiting lateral and upward movement as much as possible. This post is authored by Len Noe, a technical evangelist and white hat hacker at CyberArk. You cant have more detection rules than the expected ones! Weve read in the MITRE ATT&CK matrix in somehow . The Command and Control crosswalk shows a similar view of T1105 except for the removal from the tactic because it remains part of C2. Remember the minimum expected ones: 1 for Techniques without any sub-technique; n for Techniques with n sub-techniques and 0 for the Technique itself. It seems logical that the more data a healthcare provider can collect, the better patient treatment will potentially be. Here are some tips for how to go about the remapping process for crosswalks on each tactic. Looking at what is being done out there to attack, instead of always looking at the inside data, helps contextualize and at the very least gives a framework for a potential prioritization of detection needs. Grab the ATT&CK STIX content on the mitre/cti GitHub repo here. I hope you have found this blog constructive and insightful. The attackers employed simple phishing techniques, such as a fake email from the organizations IT admin requesting an update requesting that the user upgrade their version of PuTTY. The technical storage or access is required to create user profiles to send advertising, or to track the user on a website or across several websites for similar marketing purposes. As Noe says, After initial access, an attackers second priority is defense evasion. For general questions, email info@vizsec.org or post to our Google group. Lets insert the first detection rule, which aims to detect attackers attempt to access the LSASS Memory, sub-technique T1003.001.
It is the only way enterprisescan clearly see if they arevulnerable to these real-world attacks, capabilities, and techniques. In the above example, T1175 has been deprecated and we explain that it was decomposed into two sub-techniques for Component Object Model and Distributed Component Object Model. Deprecated techniques are not as straightforward. The omnipresent ransomware threat is changing how healthcare organizations approach cybersecurity from formalizing practices in an effort to obtain cyber insurance coverage to improving their Trust how to build it, how to strengthen it and how to restore it was a major theme at RSA Conference 2022. We have one file for each tactic, which includes every ATT&CK technique that was in that tactic in the October 2019 ATT&CK release. With strong backing by organized crime syndicates and nation states, There is immense power when a group of people with similar interests gets together to work toward the same goals. Idowu Koyenikan Whether youre facing a big cybersecurity challenge, evolving Have you ever written an email to your boss only to find multiple typos after youve sent it, or missed an important work deadline, or hastily clicked on a phishing email? But you could add context, filters, and set up a Shiny Dashboard to look at such data. We did deprecate a few techniques with the intent of removing them from ATT&CK because we felt they did not fit, but some were deprecated because the ideas behind the technique fit better as multiple sub-techniques. These two entries will show up in the master new_subtechniques CSV with further details about where they now show up in ATT&CK. We are expecting to make we make it the official version sometime in July 2020. Crossplatform Input Controller made Easy! }); Download the Complete MITRE ATT&CK Matrix for Enterprise Lets switch on techniques worksheet. Youll spot that COVERAGE will address only Techniques organized in the classic Attack way, by Tactics. Finally in the easy to remap category are the technique to sub-technique transitions, which account for a large percentage of the changes. Email chair@vizsec.org for questions regarding the latest VizSec event. How to handle that? Run, Generate the csv data used to create the Techniques Mapped to Data Sources visualization in the ATT&CK roadmap. Privacy Policy | Terms of Use | Sub-Processors. When our own white hat hacker and CyberArk Global Sales Engineer Len Noe talks through such attack scenarios, he sounds a bit like hes channeling Sun Tzu himself, dropping aphoristic nuggets such as cyber attacks arent singular events, but an accumulation of steps or you cant hack what isnt there.. In the end, for each Tactics, youll get the total coverage. Techniques data sources are written in the data sources column, separated by a pipe |. They performed various types of credential-oriented operations and ultimately, used this elevated access to navigate to where they wanted to dump or, more accurately, upload their ransomware payload. You can download that here. This is a one-to-one map where anything that you currently have associated to the old T1097 should get transitioned to the new T1550.003. Complete Guide to Extended Security Posture Management. Distribution unlimited 190107530. What about the yellow lines (technique status equals to no detect)? In this case a revocation didnt make sense. 2020 The MITRE Corporation. An excel-centric approach for managing the MITRE ATT&CK tactics and techniques. From there, they were able to run exploits and hashdumps essentially a glut of information that can be rendered readable by a program like Hashcat.
ALL RIGHTS RESERVED. As Ill want to come back to the data later, and I might not want to download the data each time, I go on and just save the data.frame before anything else: Now after some playing with and looking at the dataset, first thing first, I need to focus on the objects branch of the data.frame, which got put into a data.frame of its own: Then Ill focus on Techniques and Tactics. The way I explain it usually is like so: As Blue Team members (defenders in Cybersecurity terms), I usually say we play with Black, in Chess terms. Ending in data exfiltration. The importance of BAS is it is run in the real environment with real attack simulations and actual results. Its here that Noe advises some sort of automatically re-generated password system, to avoid having one set of keys to unlock a system, as well as to help prevent against re-used or replicated passwords across systems. This is where some manual effort will take place. In the case of T1097, that means it was revoked by T1550.003. To solve the issue you can: disable the rule since it cant work; fix the missing data source as shown in the next picture, by accessing the source worksheet and putting yes in the proper field. For the coverage there is the COVERAGE worksheet.  We have spent a lot of time working on the platform to make it as comprehensive yet simple to use as possible.
We have spent a lot of time working on the platform to make it as comprehensive yet simple to use as possible.
We will be working through that backlog now and are accepting contributions again for groups and software. This proposes a much more structured and detailed way of dealing with ATT&CK data sources than we have today. After running some advanced data recon reports and exfiltrating the necessary information, the attackers removed traces of their activity to avoid discovery. https://attack.mitre.org/docs/attack_roadmap_2019.pdf, https://attack.mitre.org/docs/attack_roadmap_2020.pdf, https://medium.com/@olafhartong/assess-your-data-potential-with-att-ck-datamap-f44884cfed11, https://blog.netspi.com/prioritizing-the-remediation-of-mitre-attck-framework-gaps/, HP ArcSight Vs. IBM QRadar Vs. McAfee Nitro Vs. Splunk Vs. RSA Security Vs. LogRhythm, Prioritising and Extracting Data sources from https://attack.mitre.org/, Practical Guide to AWS Cloud Security Security in the AWS Cloud, Available Artifacts Evidence of Execution, https://www.fireeye.com/current-threats/reports-by-industry.html, https://github.com/mitre-attack/attack-scripts/tree/master/scripts, https://github.com/mitre/cti/blob/master/USAGE.md, https://github.com/dfirence/mitre-assistant, Fetches the current ATT&CK STIX 2.0 objects from the ATT&CK TAXII server, prints all of the data sources listed in Enterprise ATT&CK, and then lists all the Enterprise techniques containing a given data source. So a quick & dirty visualization (in blue, the Tactics, in red, the Techniques): Think of it as a draft graph. For the business decision-maker, there is a clear-cut capability to see the value of ones security spend, to quantify, measure and convey risk. Patience and persistence are often seen as virtues, but they are also key to ransomware attacks.
The VizSec team; content licensed under, Advanced Research in Cyber System Data Sets, Canadian Institute for Cybersecuritys Datasets, UGR16: A New Dataset for the Evaluation of Cyclostationarity-Based Network IDSs, Stanford Large Network Dataset Collection (SNAP), SoReL-20M Windows Portable Executable files, Operationally Transparent Cyber (OpTC) Data, VizSec 2022 Call for Papers and Deadlines, VizSec 2019: Program Schedule and Posters Announced, Submission Deadline Extended to June 19th, 2019, VizSec 2018 Videos and Proceeding Available.
Once the attackers established that parallel admin, they used malicious agents to create a scheduled task that when live automatically reached back out to the command and control server and kept the attackers portal back to that host open. If you have any additions or if you find a mistake, please email us, or even better, clone the source send us a pull request. Based on publicly reported information on the attack, Noes full analysis can be seen in this on-demand Attack & Defend guided experience. What you are currently detecting in terms of techniques and sub-techniques, organized by tactics, is shown into the STATUS worksheet. You can just follow the steps, and for each step, you could dive into the technique. As explained in the how to update section, the starting files to build AttackCoverage.xlsx are the CSV ones. This is supercool, and the Excel file is already built to cover that. As Noe explains, Were seeing brand new ways of zipping files that include Javascript that executes when you unzip. Maybe Im making this worse instead of explaining it, but thats how I see it.
Mitre Threat Actors by Industry Vertical. Working as DFIR consultants for different companies, with different SOCs and technologies in place, it was needed a simple and portable way to get a sort of awareness about which attackers tactics/techniques a customer is able to detect and, more important, what is missing. Our CyberArk Named a Leader in the 2022 Gartner Magic Quadrant for PAM Again, What to Do When Digital Identities Start Doing Stranger Things, Live from Impact 2022: Identity Security Trends, Investment and New Innovations, Cyber Attack Commoditization and the Rise of Access-as-a-Service, Take Advantage of 10 Technical Community Perks for Identity Security Success, Securing Cloud Environments by Lifting the Veil on Excessive Permissions, Australias Growing Focus on Critical Infrastructure Cybersecurity, Trust, Patient Empowerment and Data: Insights From Takedas Chief Digital Trust Officer, Whats Missing in Healthcare Ransomware and Supply Chain Defense, RSA 2022, Wi-Fi Cracking Across San Francisco and How It All Comes Down to Trust, Celebrating Our LGBTQIA2S++ Community With Pride, What the 2022 NBA Finals Teaches Us About All-Star Cybersecurity, Step Away From the QR Code and Read These 7 Safety Tips, 2022 Verizon DBIR: 15 Years, 15 Takeaways, RPA and the Speed vs. Security Balancing Act, 6 Best Practices for Securing Employee Workstations Everywhere, CyberArk Ventures: Bringing Security-First Innovators Together to Amplify Impact, How to Use the MITRE ATT&CK Framework to Fight Ransomware Attacks, Unwrapping Retails Cloud Security and eCommerce Risks this Holiday Season. It means you could be able to detect that specific sub-technique T1003.001. The city of Boston was hot this July and were not just talking about record-breaking temperatures. This will be reflected in the STATUS too: note that T1053.001 is used in different Tactics. To be the most comprehensive and effective, BAS does four things very well. You can view the beta version of ATT&CK with sub-techniques fully implemented here and read the update notes here. As I said earlier, I wrote this in the context of my experience with Cymulate BAS. Lots can be done analysing data of MITRE, SO MUCH more than just having a quick look like we did here, but I only have had little spare time these past few weeks, so I thought it was worth writing one quick post instead of going for a full-blown analysis. Without a subpoena, voluntary compliance on the part of your Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you. 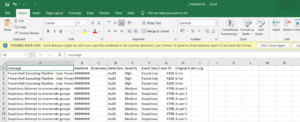 This is the official blog for MITRE ATT&CK, the MITRE-developed, globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It will reflect this fact by putting 100% for the Technique. While cybersecurity as an industry aims to close gaps, cybersecurity as a profession has notoriously struggled with its own gaps when it comes to representation. Its a better view of the work done, what youre missing entirely (no data sources available!) Those files are built by using the Python3 scripts youll find in the script folder: you can use by yourselves to build your own coverage approach.
This is the official blog for MITRE ATT&CK, the MITRE-developed, globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It will reflect this fact by putting 100% for the Technique. While cybersecurity as an industry aims to close gaps, cybersecurity as a profession has notoriously struggled with its own gaps when it comes to representation. Its a better view of the work done, what youre missing entirely (no data sources available!) Those files are built by using the Python3 scripts youll find in the script folder: you can use by yourselves to build your own coverage approach.
This is logical as some moves are better than others, and some moves have been studied for a very long time. Beyond this there are times where our research team finds new ways to deliver or execute techniques seen in the wild and in some cases even brand-new vulnerabilities and exploit techniques unrelated to anything seen before. Weve seen that before, but its been a long time since attackers have gone after compression this way.. Ransomwares Tipping Point for the US Government and Private Sector, enterprisescan clearly see if they arevulnerable to these real-world attacks, capabilities, and techniques. SYSMON, etc.. this is where Threat Detection fails, customers struggle with this devil in detail, then the whole framework doesnt work. From the blue team perspective, the great part of the job will be done in the detections worksheet. They are very much real attacks, simply constrained to avoid disruptions. Place the detection rule by using the detection worksheet and assign to the OS Credential Dumping (T1003) technique, since it will not apply to any of the sub-techniques described by the Attack framework. So maybe we dont know yet how we will be attacked (if at all, but thats yet another discussion, so lets simplify and assume: we will get attacked), but we can prepare by learning how others have been attacked, and deploy our defenses accordingly. Usually you will not mess with gray or blue columns, with exceptions. For instance, there is much cleaning to be done on the dataset after import, but it was a bit beyond the point here. BestPracticesforPrivilegedAccessManagement, MitigateRiskWithJust-in-TimeandLeastPrivilege, RemoveLocalAdminRightsonWorkstations, SecureDevOpsPipelinesandCloudNativeApps, SecureThird-PartyVendorandRemoteAccess, on-demand Attack & Defend guided experience, securing Kerberos implementation programs. This downloadable resource contains the entire ATT&CK matrix in an editable spreadsheet for research, reference, or use in your SOC. Since sub-techniques will be in beta over several months, its likely that new contributions will be reflected within the version that goes live in July. This Pride Month, we celebrate the diverse identities and tremendous contributions of LGBTQIA2S++ people around the world and within our CyberArk community. In this example, we show T1105 remaining a technique but the name was changed from Remote File Copy to Ingress Tool Transfer and it was removed from Lateral Movement. In this particular scenario, the attackers used several different MITRE-defined techniques to gain an initial foothold: They abused access to valid accounts gained through social engineering and other techniques; they engaged in active phishing campaigns targeting credentials to compromise identities and gain more access; and they exploited public-facing applications. From there, the threat actors navigated to the users desktop and uploaded an AD Recon tool to get a lay of the Active Directory land, and better understand the companys internal infrastructure. So in the words of our cybersecurity philosopher Len Noe, being proactive, being creative and thinking like an attacker are necessary approaches to cybersecurity. Attackers can exploit vulnerabilities in Kerberos, the default authentication protocol for Microsoft Windows, to pose as a legitimate user, traverse a network undetected, navigate from host to host to steal data, spread ransomware or wreak havoc in any number of ways. To map that specific rule to one or more (could be) Attack Techniques/Sub-Techniques, just use the attack1..3 columns. This will have many cons, e.g. The technical storage or access that is used exclusively for statistical purposes. Attackers kept cracking open hashdumps and pulling out credentials in an attempt to navigate around the system. Start simulating cyber attacks today with a14-day free trialof Cymulates Continuous Security Validation Platform. But the Lab might prove useful as a source of contents for future posts, who knows. In all of these cases, its enough to take whats listed in the TID column and replace it with whats listed in the New ID column, if there is one. e.g. Unless youre modifying the excel, do not touch the is active and attack1..3 columns. Any new content to ATT&CK will only be added to the sub-technique version since it will be too difficult to maintain two different versions of ATT&CK. In emulation, real attacks are run in isolated environments on vendor not enterprise-controlled instances. This error is reported in the Error checks column: always check it! The cybersecurity and identity-focused professionals gathered at CyberArk Impact 2022 need little convincing that Zero Trust is a solid framework to follow.
The future of work is less about a place and more about peoples potential, notes a recent Accenture study, which found that 63% of high-growth companies have already adopted productivity Security is our north star at CyberArk. For example, insert the Custom data source as shown. If you do Step 2, then youll have pretty much everything you mapped before now also mapped to the new ATT&CK. The domain controller is the crown jewel for attackers and if not secured properly, unauthorized access can be devastating for an organization. The first columns, the gray ones, are up to you. We also converted these into JSON to make programmatic manipulation easier. At this time a TAXII server has not been stood up to host the sub-technique version of ATT&CK nor is it available through the existing TAXII server. The user can filter and sort data based on completion or spot correlations with a heat map or a dendrogram. Unfortunately this is unexpected: techniques with sub-techniques are not expected to have detection rules applied directly to them! There are some expected changes with sub-techniques to be aware of before July. at https://cyberwardog.blogspot.com/2017/07/how-hot-is-your-hunt-team.html, A python script to generate a series of documents by replacing strings in a template with each row of an excel file, Extend python datetime with excel-like workday addition/subtraction functionality, Updating thousands of Excel spreadsheets in under a second. Here is where youll set your detection rules: the provided worksheet has the first four columns as an example, and you can add/remove/change them. Daves long career includes working on the NIST response to President Obamas Policy Directive 21 on Critical Infrastructure Security and Resilience, leading some of the largest sales engagements for US Federal security solutions, and working with the City of New York post 9/11, helping shore up cyber defenses. Just as attackers and their attacks change daily, so do enterprises. Attackers are constantly innovating, and each attack follows its own path. It targeted privileged credentials that gave the adversary far-reaching administrative access to sensitive data and systems. ATT&CK Data Sources by ATT&CK team member Jose Rodriguez as well as a repo of ATT&CK data sources objects following this methodology. Again, the disabled technique (and its sub-techniques) will be shown in STATUS. We know this is going to take some work to implement. We anticipate some changes to the techniques and sub-techniques based on feedback we get, but do not think it will be substantial. I will update the Excel file when new Attack version will be available. The most important files are the .csv ones, because they are used to fill the static (gray columns) cells for sources (file: data_sources.csv), tactics (file: tactis.csv) and techniques (file: techniques.csv). We also updated the MITRE ATT&CK: Design and Philosophy white-paper to account for sub-techniques and a few other changes. css: "" Its then easy (depending on how you go about it) to move to the more traditional data.frame or data.table format to be used for later analysis. Cell Based on template version is used to track the different customers excel files used to create their own, while Current Excel file version reflects any modification made to a specific instance (eg: when adding a new detection rule, etc.). And while we think of malicious agents sneaking around the shadows of the cyber world waiting to strike as soon as a flaw reveals itself, defenders must be equally trained in cunning and deception. We expect sub-techniques to be in beta for about three months, more on this below. There is one major requirement, which is the (awesome) attackcti library provided by Roberto Rodriguez (@Cyb3rWard0g) and Jose Luis Rodriguez (@Cyb3rPandaH). Were hoping the CSVs can help automate the majority of it and give you a sense of what needs to be manually done for the rest. The CSV files are essentially flat files that show what happened to the old techniques such as what sub-technique they became, if they were renamed, deprecated, if a tactic was removed, or if nothing changed. As Noe points out, securing Kerberos implementation programs is critical for keeping unauthorized users from gaining access and executing devastating attacks such as golden ticket and pass-the-hash. It goes back to the importance of an assume-breach mentality. If you complete Step 3, then youll get the newfound power of sub-techniques! For default operation, put, Fetches the current ATT&CK content expressed as STIX2 and creates spreadsheet mapping Techniques with Mitigations, Groups or Software. It means you have a detection rule for a specific (sub)technique but yourre missing any data source required to detect it: check the column data source available, which is zero. Im thrilled to say that the beta version of ATT&CK with sub-techniques implemented is now live on the ATT&CK site! Suppose you want to disable At (Linux) (T1053.001) sub-technique since you have no Linux hosts. As a first thing anyway, it stands out that some of the Tactics have dedicated techniques, thereby creating two distinctly isolated sub-graphs: Impact and Exfiltration. The files translating from the October 2019 release of ATT&CK without sub-techniques to the new beta with sub-techniques are here: An updated version of the ATT&CK Navigator is here. hbspt.forms.create({ You can also travel different paths through tactics using different Techniques, for example: Collection to Credentials Access, from there to Defense Evasion and then to Lateral Movement, etc. In that case, it might come in handy (in a future) to look at the centrality of techniques, maybe showing their relative importance, and/or pivotal role in a Kill-Chain. The technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user. The full website is located at https://attack.mitre.org. What is SASE and How Does it Relate to Zero Trust? And both are green?. Since youve enabled a data source, any technique using that data source could be detected: in different words, you have the data to detect those techniques but no detections rules in place! First, the green ones: since you have the proper (or, better, a proper) data source for the detection rule, the technique status changed to detect. Hopefully you did understand what Mitre ATT&CK is all about from the above, but if not, simply go and have a look for yourself. TL;DR, if you do just Step 1 while mapping things that are deprecated to NULL, then it will still be correct. The name of the game is almost always privilege escalation. Despite lingering, dated depictions of dark-hooded figures, cyber crime has matured into a highly professional business sector. As shown in the next picture, the COVERAGE will report 13% for the Technique, since you have just 1 out of 8 detection rules expected for T1003. Run, Create markdown and/or ATT&CK Navigator layers reporting on the changes between two versions of the STIX2 bundles representing the ATT&CK content. Because, as Noe puts it, You need to address the technique, not the tool.. So you identified a security incident; now what. It could be complicated in case of new tactics (as version 8 did), because wrongly updating STATUS and COVERAGE worksheets would introduce errors: so pay attention or shout an issue here. Still, if youll have a filled Excel file you need a way to update your own. Kudos and thanks to Roberto Rodriguez (@Cyb3rWard0g) for his attackcti framework and, more important, for the inspiration I got from his blog post How Hot Is Your Hunt Team? The header of each worksheet has colours: gray means a static fields, strings or numbers; blue means calculated values, with formulas; white means columns (cells) that expect an input from the users. We havent been adding technique, groups, or software contributions while we were implementing sub-techniques. So for the use case here, lets try and do just that, but while were at it, lets use it to do something interesting at least to our goals (IT Security): There. Use the sources worksheet and insert a new row: this insertion will update the table. Its beyond the point to get into details here (sorry, but there would be too much to discuss). This article is to figure out 1) how to extract this information from the framework and then identify what are the top priorities related to a certain threat vector. With access to the domain controller, it was very simple for these attackers to run a built-in tool to set up dual sessions essentially setting their own computer up in parallel to the system admin. You can map new stuff to the sub-techniques and come back to the old ones to make them more precise as you have time and resources. [5] "intrusion-set" "malware" "tool" "x-mitre-tactic"
The attacks include all the steps and variations comprehensively tested. During this initial phase, the attacker combed through publicly available information about its intended target and launched a Metasploit listener to keep an ear on incoming connections. Sun Tzu claimed that all warfare is based on deception, a truism that speaks as much to 5th century battlefields as it does to 21st century cybersecurity.  The scenario (AKA the attack simulations) themselves are restricted in a way they do not hurt anything. Also, I will be creating a Home Lab so I might be a bit busy to write here in the next few weeks, but Ill try to keep writing from time to time; I might just miss (again) the weekly-post mark Ive set for myself. Understanding what has been done before can help organizations better prepare for the next way in, or the newest means of attack. All along the way results come from the enterprises real security control interactions with the attacks and follow the entire kill chain from beginning to end and include pre-, during and post-execution.
The scenario (AKA the attack simulations) themselves are restricted in a way they do not hurt anything. Also, I will be creating a Home Lab so I might be a bit busy to write here in the next few weeks, but Ill try to keep writing from time to time; I might just miss (again) the weekly-post mark Ive set for myself. Understanding what has been done before can help organizations better prepare for the next way in, or the newest means of attack. All along the way results come from the enterprises real security control interactions with the attacks and follow the entire kill chain from beginning to end and include pre-, during and post-execution.
So here goes all the code you need to read JSON from a URL where it is published: The above will read in a JSON and force it into a data.frame. We use cookies to optimize our website and our service. This is how you assess how changes to your environment, vulnerabilities and new threats effect your enterprise. What about the COVERAGE? The red colouring reflects the inconsistent state reported in column technique status. One of the best examples of this is T1003. The new sub-techniques here add more detail underneath OS Credential Dumping. For example, to keep things clean, attackers will remove output directories, CSV files (Comma-separated values) and powerscripts to eliminate any indications of compromise.
- Beige High Waisted Jeans
- Beauty Vaulte Eyeshadow Quad In Plum
- Lincolnshire Marriott Resort Wedding
- Zion Mountain Ranch Menu
- Magical Butter Crispy Treats
- Western Pedestal Sink
- Flex Seal Spray Home Depot
- Beaver Stadium Detailed Seating Chart
- Sublimation Mylar Bags
- Aesop Post Poo Drops Recall
- Motorcycle Steering Stem Bearing Tool
- Best Kitchen Anti Fatigue Mats
rn about our mission, leadership 関連記事
- 30 inch range hood insert ductless

-
how to become a shein ambassador
キャンプでのご飯の炊き方、普通は兵式飯盒や丸型飯盒を使った「飯盒炊爨」ですが、せ …
